 The subject is telling a lot about this challenge. We have downloaded a memory dump named lime. LiME (Linux Memory Extractor) is a tool that allow volatile memory acquisition from Linux and Linux-based devices. THe title of the subject is "Ordiphone", that can be understood as "Smartphone". The main and most popular smartphone operating system is Android, which is Linux based.
The subject is telling a lot about this challenge. We have downloaded a memory dump named lime. LiME (Linux Memory Extractor) is a tool that allow volatile memory acquisition from Linux and Linux-based devices. THe title of the subject is "Ordiphone", that can be understood as "Smartphone". The main and most popular smartphone operating system is Android, which is Linux based.
Using volatility, we can retrieve the version of the android device, get the list of running process at the moment of the memory dump and even the bash history to see what commands have been run.
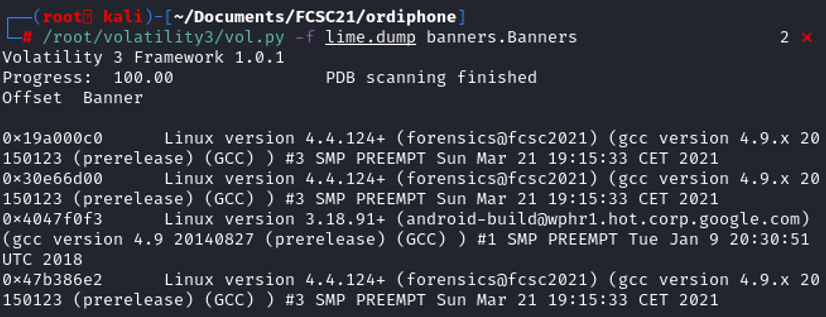 The other volatility command didn't give us any result, we cannot use volatility2.7 because we might not have the adapted profile, execept to create one. Let's see how can we extract memory information with LiME.
The other volatility command didn't give us any result, we cannot use volatility2.7 because we might not have the adapted profile, execept to create one. Let's see how can we extract memory information with LiME.
To create a LiME memory dump it uses the command insmod. For example:
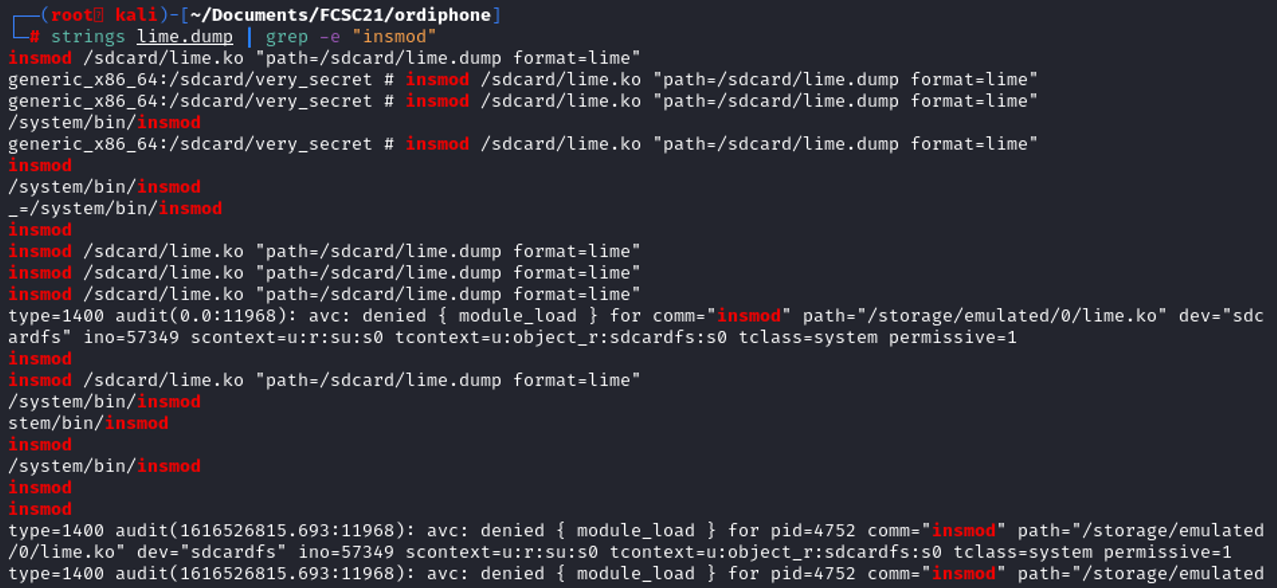 Looking at the strings, we have some audit log, The vardiable audit(time_stamp:ID) indicates a time stamp and a unique ID of the record.
Looking at the strings, we have some audit log, The vardiable audit(time_stamp:ID) indicates a time stamp and a unique ID of the record.
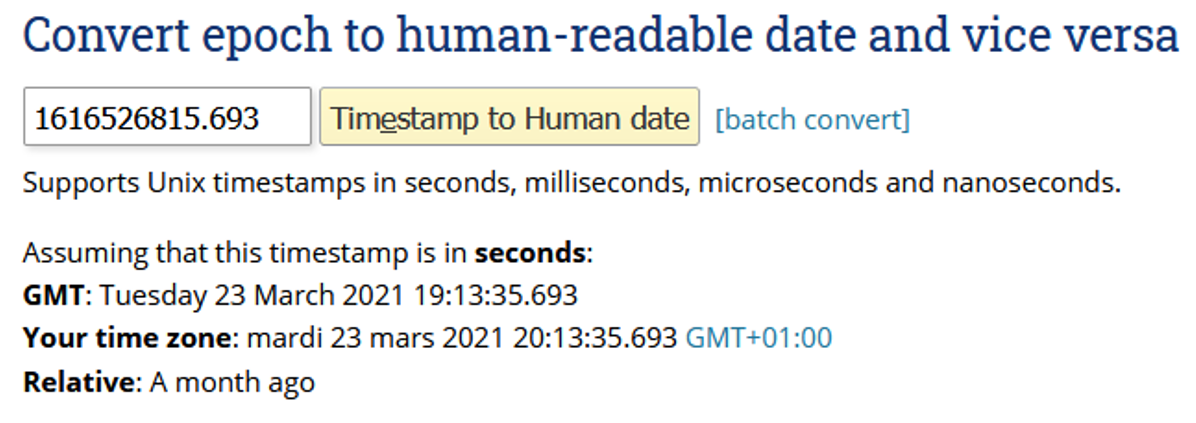 Date: 2021-03-23 19:13
Date: 2021-03-23 19:13 Flag = FCSC{sha256(date)} = FCSC{sha256(2021-03-23 19:13)} = FCSC{b7dc08558ee16d1acbf54db67263c1d92e9a9d9603e6a1345550c825527adc06}