 The challenge comes with two files. We have the code used for encryption and the output (encrypted message). The goal is to decrypt the encrypted message.
The challenge comes with two files. We have the code used for encryption and the output (encrypted message). The goal is to decrypt the encrypted message.
import os
from Crypto.Util.number import
long_to_bytes
from Crypto.Util.strxor import strxor
FLAG = open("flag.txt", "rb").read()
key = os.urandom(4)*20
c = strxor(FLAG, key[:len(FLAG)])
print(c.hex())
Reading the code, the encryption method using by this file is XOR. strxor(str a, str b) return the a XOR b. Both parameters must have the same lenght. This is why the second parameter is a slice of the array key depending on the lenght of the FLAG. from Crypto.Util.number import
long_to_bytes
from Crypto.Util.strxor import strxor
FLAG = open("flag.txt", "rb").read()
key = os.urandom(4)*20
c = strxor(FLAG, key[:len(FLAG)])
print(c.hex())
The variable key is taking 4 random value, and it is going to repeat 20 times. We also know that the FLAG always start with FCSC.
With XOR encrytpion, as long as we have 2 elements, we can determine the 3rd one.
INPUT XOR KEY = OUTPUT
OUTPUT XOR INPUT = KEY
OUTPUT XOR KEY = INPUT
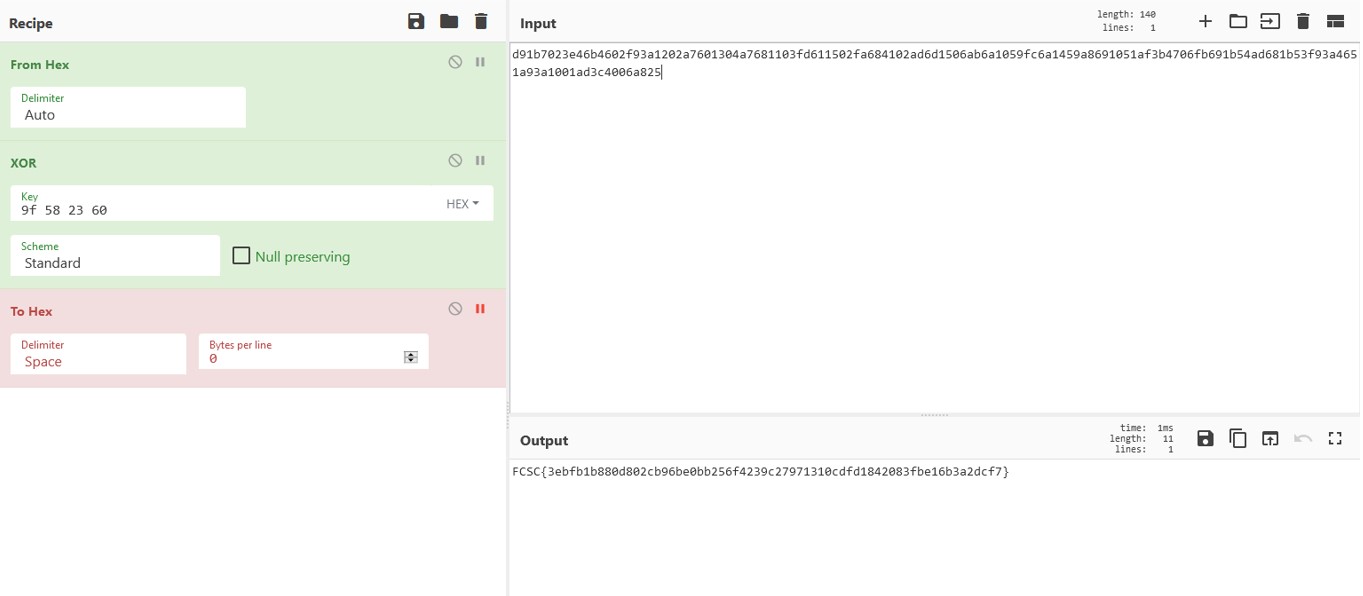
In our case, we don't know the key, we only have the output file and we know that the flag starts with FCSC. Therefore, if we XOR the four first characters of the output with FCSC then we should get the key.
OUTPUT XOR INPUT = KEY
OUTPUT XOR KEY = INPUT
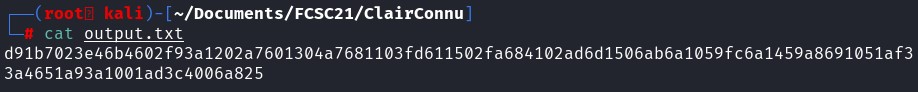
OUTPUT XOR INPUT
= \xd9\x1b\x70\x23 XOR hex(FCSC)
= d91b7023 XOR 46435343
= 9f582360
Key = 9f 58 23 60. Now let's determine the flag by xoring the output with the key.
= \xd9\x1b\x70\x23 XOR hex(FCSC)
= d91b7023 XOR 46435343
= 9f582360