The given resource is a .vmem file. Volatility is a tool that can be used to retrieve some crucial information on the memory image.
If you are using volatility2, you need to determine the profile used for the memory analysis.
vol.py -f Bob.vmem imageinfo
The profile used will be WinXPSP2x86. What was the local IP address of the victim's machine ?
When analyzing a suspicious system, it is interesting to know if the system is communicating with a suspicious IP address.vol.py -f Bob.vmem --profile=WinXPSP2x86 connections
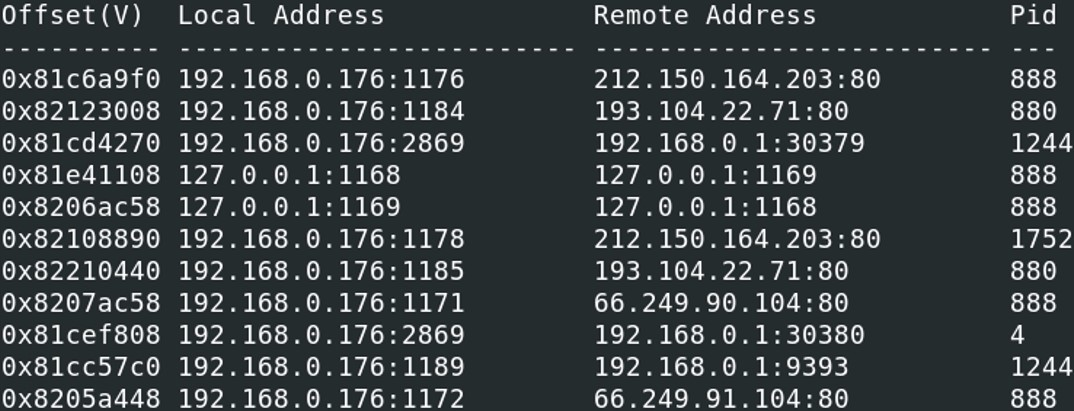
What was the OS environment variable's value ?
The function envars in volatility displays the environment variable of the system.vol.py -f Bob.vmem --profile=WinXPSP2x86 envars | grep OS
What was the Administrator's password ?
In a Windows system, it exists several registry hives. The ones that interest us to recover the password are the SAM (-s) and the SYSTEM (-y) hives. First we must list the registry hives.vol.py -f Bob.vmem --profile=WinXPSP2x86 hivelist
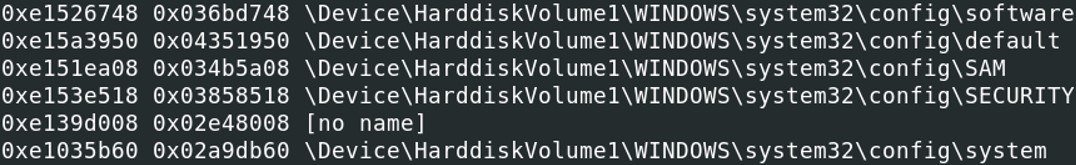 The virtual address of the SAM hive is 0xe151ea08 and the virtual address of the system hive is 0xe1035b60.
The virtual address of the SAM hive is 0xe151ea08 and the virtual address of the system hive is 0xe1035b60. Now that we have the virtual addresses of the SAM and system hives, we can proceed to the password cracking of the system.
vol.py -f Bob.vmem --profile=WinXPSP2x86 hashdump -y 0xe1035b60 -s 0xe151ea08
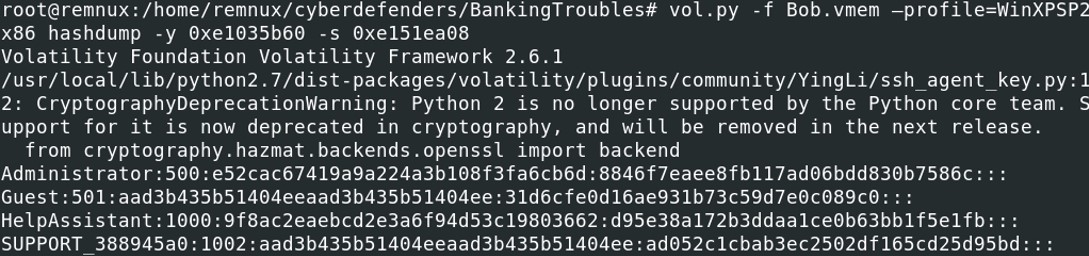 Administrator:500:e52cac67419a9a224a3b108f3fa6cb6d:8846f7eaee8fb117ad06bdd830b7586c:::
Administrator:500:e52cac67419a9a224a3b108f3fa6cb6d:8846f7eaee8fb117ad06bdd830b7586c::: Here is the structure of the hash : Username:SID:LMhash:NThash
The difference between LM and NT hashes is that the LMhash is case insensitive while NThash is case sensitive. LMhash support only 142 characters while NThash support 65536 characters.
With the retrieved hash, let's use the tool John the Ripper to crack it.
john --format=NT -w=/usr/share/wordlists/rockyou.txt hash.txt --pot=output.txt
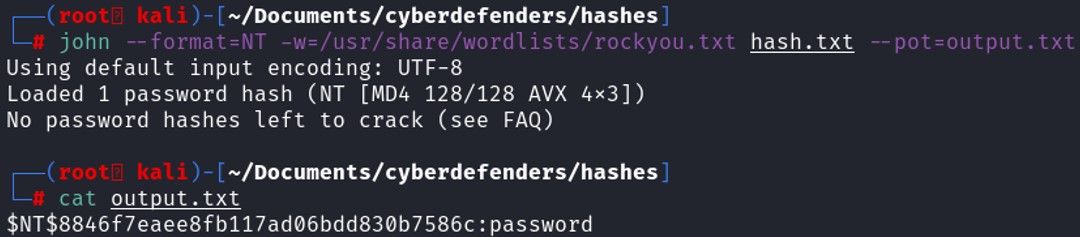 The administrator's password is "password".
The administrator's password is "password". Which process was most likely responsible for the initial exploit ?
To look closely to the process running, pslist, pstree can be used to list the running process at the time the memory dump has started.vol.py -f Bob.vmem --profile=WinXPSP2x86 pstree
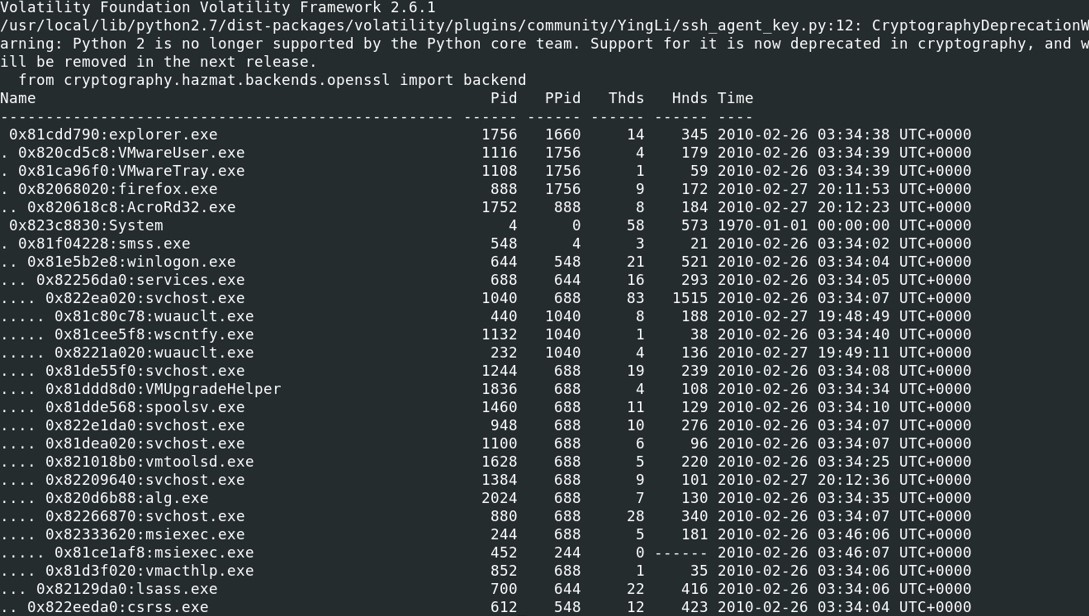 AcroRd32.exe has been launched by firefox.exe, which shouldn't be the case for a legitimate Acrobat Reader program.
AcroRd32.exe has been launched by firefox.exe, which shouldn't be the case for a legitimate Acrobat Reader program. The process ID of the AcroRd32.exe is 1752, and its parent process ID is 888. Let's take a look at the remote connection to see if the program is connected to a suspicious IP address.
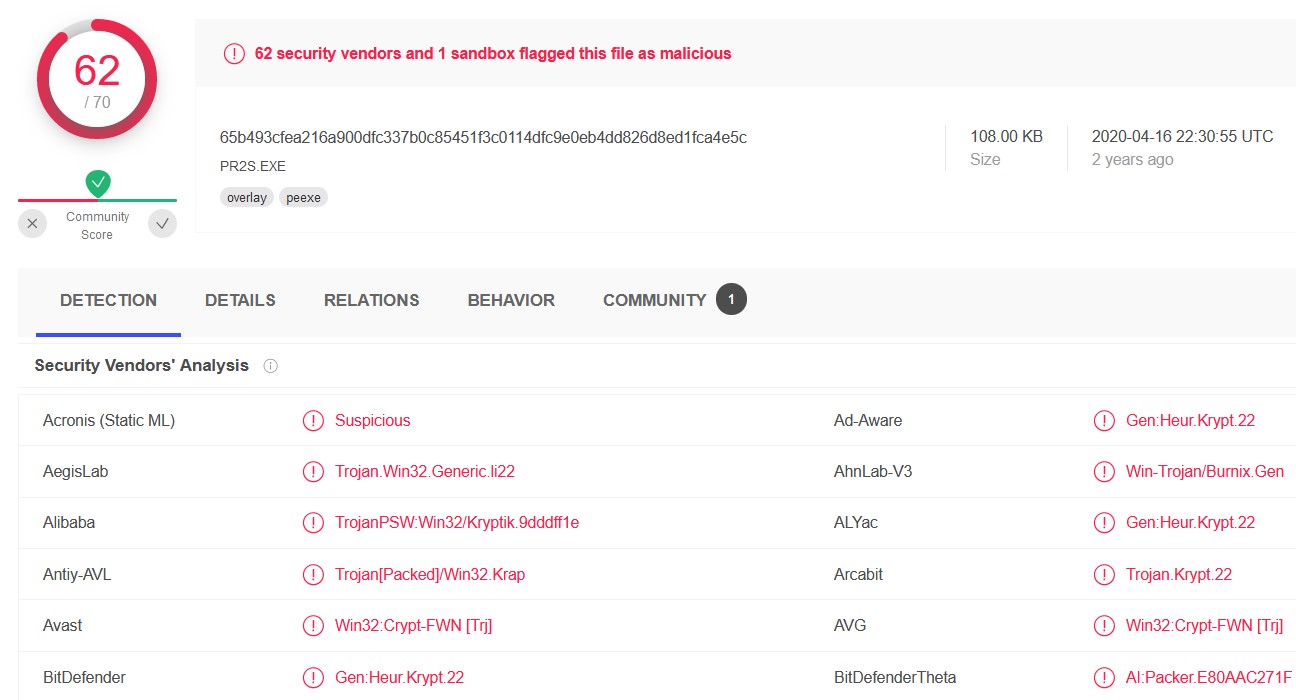
vol.py -f Bob.vmem --profile=WinXPSP2x86 connections | egrep "^Offset|888|1752"
Taking a look at the open network connection, we notice that the IP address 212.150.164.203 on the port 80 appear twice with both PIDs.
A suspicious URL was present in process svchost.exe memory. Provide the full URL that points to a PHP page hosted over a public IP (no FQDN).
Looking at the open network connection of the system, we see that there is another process ID (880) that remotely communicate with another suspicious IP address.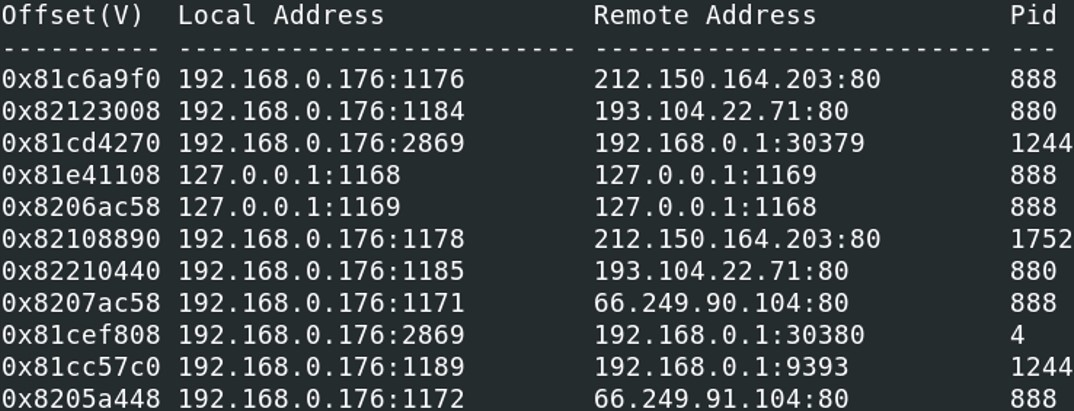 Listing the processes shows that the PID 880 belongs to a svchost.exe process.
Listing the processes shows that the PID 880 belongs to a svchost.exe process.
 Yarascan is a volatility plugin that scan a memory image for a yara signature. First, let's create a yara rule that will trigger in case of a http/https detection.
Yarascan is a volatility plugin that scan a memory image for a yara signature. First, let's create a yara rule that will trigger in case of a http/https detection.
rule findhttp{
meta:
author="HakkYahud"
description="Finding malicious http(s)"
create="09/08/2022"
&strings:
$https="https://"
$http="http://"
$php=".php"
condition:
($https and $php) or ($http and $php) }
meta:
author="HakkYahud"
description="Finding malicious http(s)"
create="09/08/2022"
&strings:
$https="https://"
$http="http://"
$php=".php"
condition:
($https and $php) or ($http and $php) }
vol.py -f Bob.vmem --profile=WinXPSP2x86 -y findhttp.yar yarascan -p 880
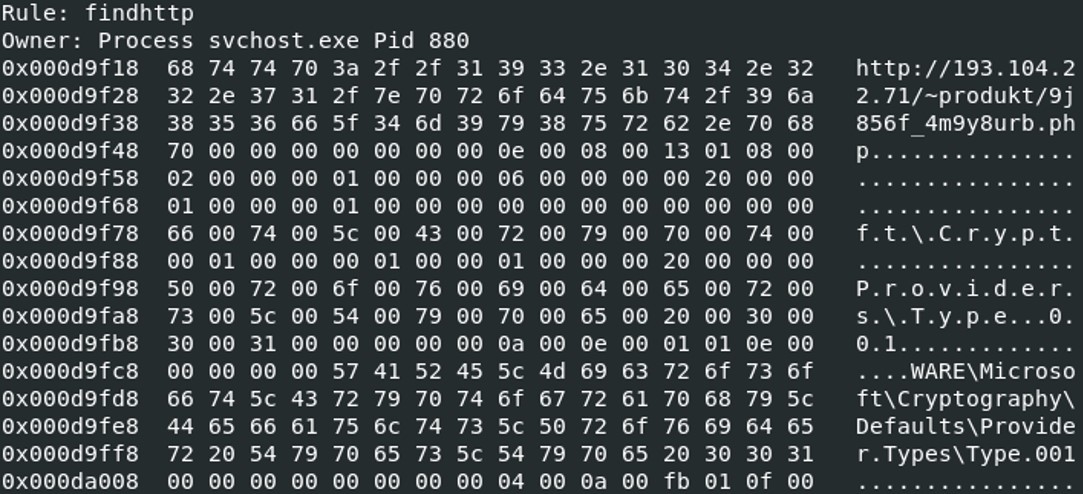 The result of the yarascan on the process 880 has found an URL "hxxp[:]//193[.]104[.]22[.]71/~produkt/9j856f_4m9y8urb[.]php".
The result of the yarascan on the process 880 has found an URL "hxxp[:]//193[.]104[.]22[.]71/~produkt/9j856f_4m9y8urb[.]php". Extract files from the initial process. One file has an MD5 hash ending with "528afe08e437765cc". When was this file first submitted for analysis on VirusTotal?
The initial exploit process is AcroRd32.exe with a PID 1752. To start we will dump this process.vol.py -f Bob.vmem --profile=WinXPSP2x86 memdump -p 1752 -D ./dumps
Once the memory dump has been retrieved, foremost is a great tool to extract the content of the memory dump, it will recover the files by looking at the headers, footers and internal datastructure of the memory or disk images.
foremost -t pdf 1752.dmp
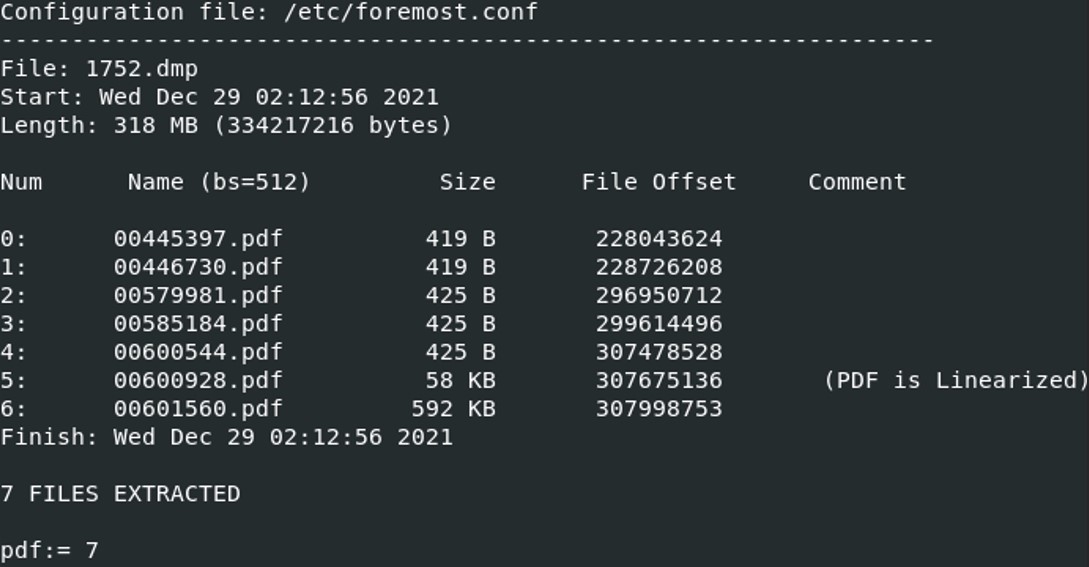 Foremost found and extracted 7 pdf files. We must find the file that has a hash ending with "528afe08e437765cc".
Foremost found and extracted 7 pdf files. We must find the file that has a hash ending with "528afe08e437765cc".
md5sum * | grep 528afe08e437765cc
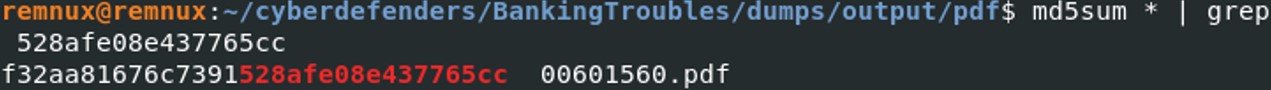
What was the PID of the process that loaded the file PDF.php?
We have extracted the memory dump of the process AcroRd32.exe, let's take a look at the string of that memory dump.Strings 1752.dmp | grep PDF.php
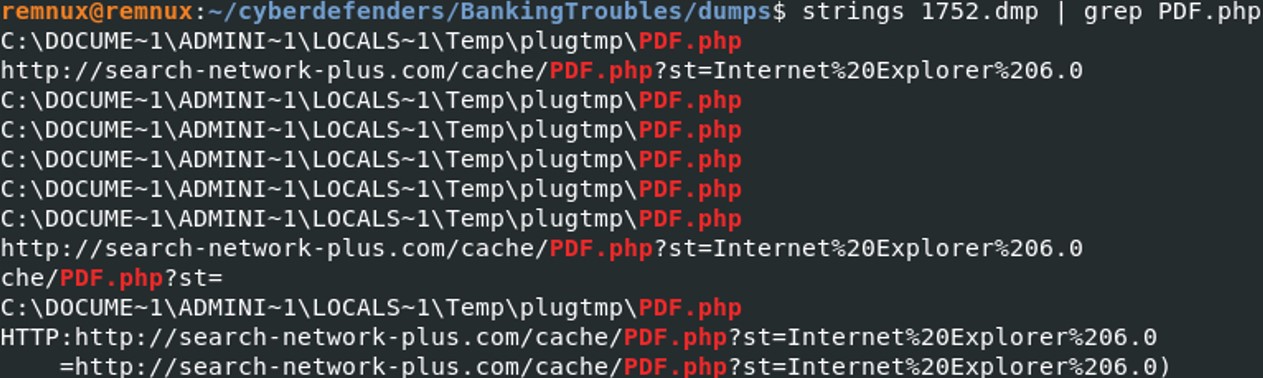 Many PDF.php is found in the strings of the process, which indiicates that the program might use "PDF.php" during his execution. The domain "http://search-network-plus.com/cache/PDF.php" could indicate that the program will download the file PDF.php in this domain.
Many PDF.php is found in the strings of the process, which indiicates that the program might use "PDF.php" during his execution. The domain "http://search-network-plus.com/cache/PDF.php" could indicate that the program will download the file PDF.php in this domain. Let's see if the file is present in the system when the memory dump has been dump. Filescan is a volatility plugin that allows the scan of all the file in the memory dump.
vol.py -f Bob.vmem --profile=WinXPSP2x86 filescan | grep PDF.php
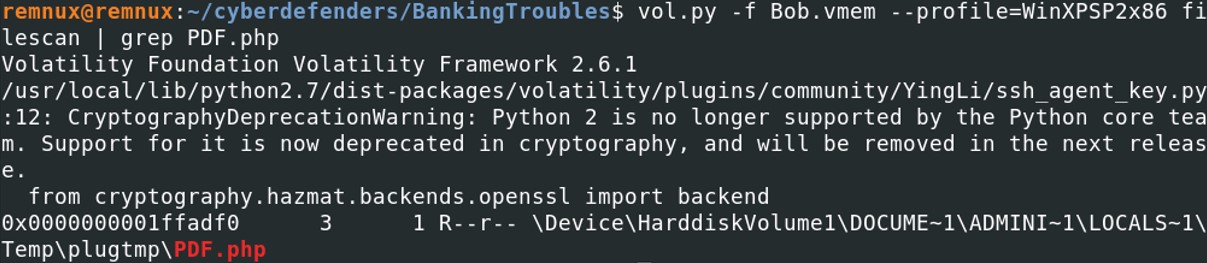 Virtual address of the file : 0x0000000001ffadf0
The plugin dumpfile is used to dump a file in volatility.
Virtual address of the file : 0x0000000001ffadf0
The plugin dumpfile is used to dump a file in volatility.
vol.py -f Bob.vmem --profile=WinXPSP2x86 dumpfiles -Q 0x0000000001ffadf0 -D ./dumps
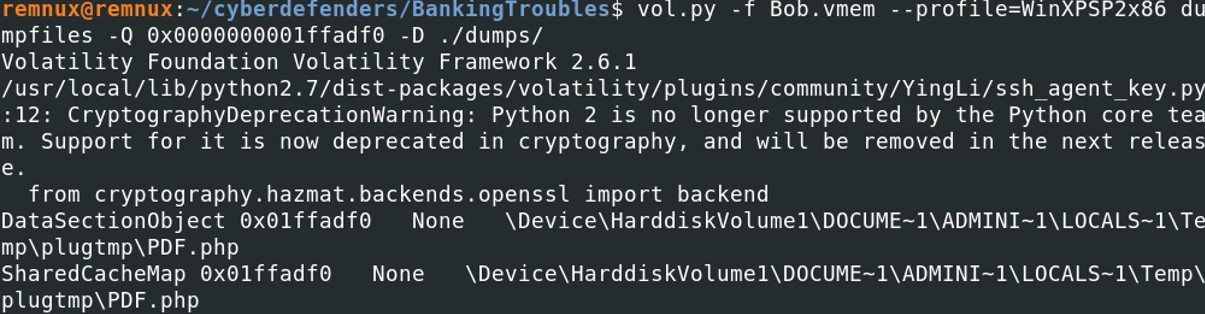 We have extracted the file, to know the file type on a UNIX device, type file [FILENAME], or we can also check the header of the file by using hexdump or xxd.
We have extracted the file, to know the file type on a UNIX device, type file [FILENAME], or we can also check the header of the file by using hexdump or xxd.
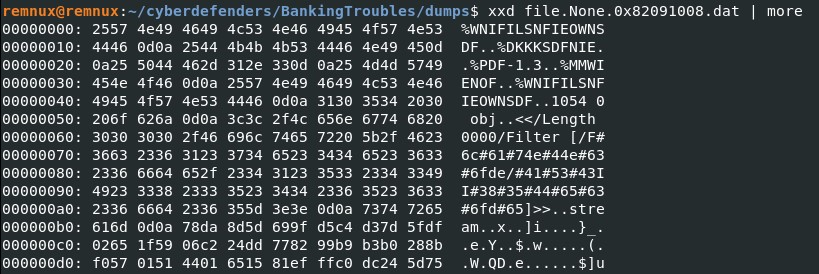 The file extension is .php on the file name, but it is actually a .pdf. To analyze pdfs, Didier Stevens has created a tool called "PDFid". It can retrieve any embedded object inside of the PDF file.
The file extension is .php on the file name, but it is actually a .pdf. To analyze pdfs, Didier Stevens has created a tool called "PDFid". It can retrieve any embedded object inside of the PDF file.
pdfid.py [FILENAME]
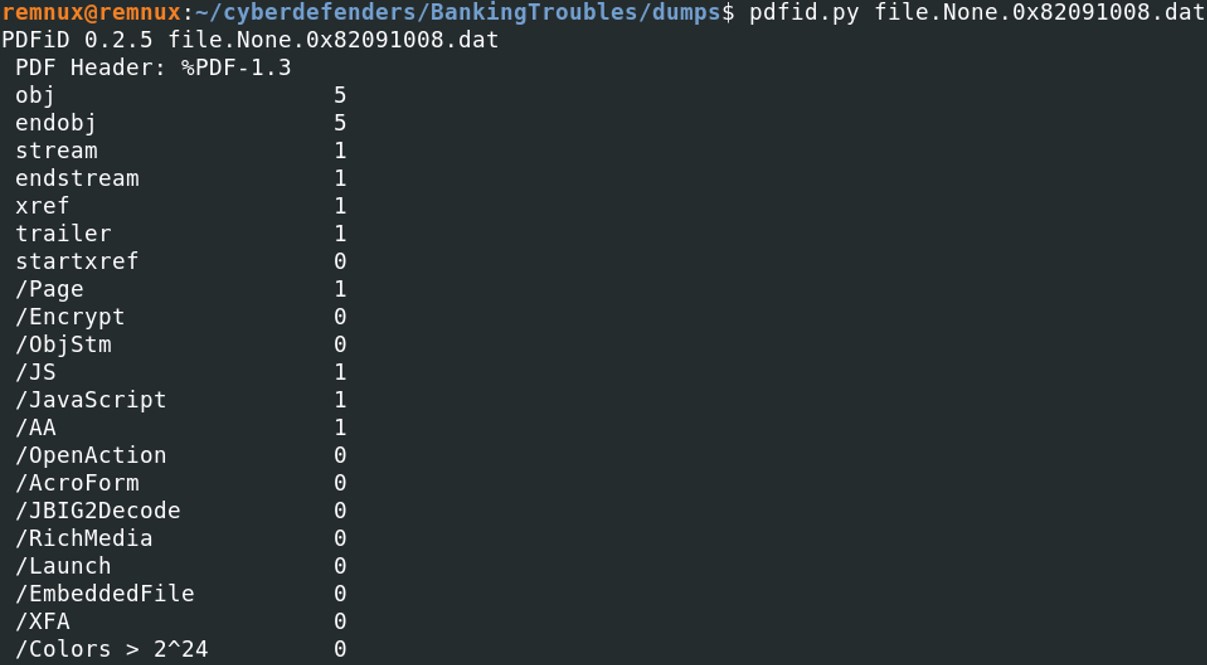 The pdf contains some Javascript since there is a embedded object that belongs to the category JavaScript / JS.
The pdf contains some Javascript since there is a embedded object that belongs to the category JavaScript / JS. To extract the JavaScript inside of the PDF, we will use peepdf. Peepdf required a script to extract the pdf. The script will be written in a file called "extractjs.txt".
Echo "extract js > javascript_extracted.pdf" > extractjs.txt
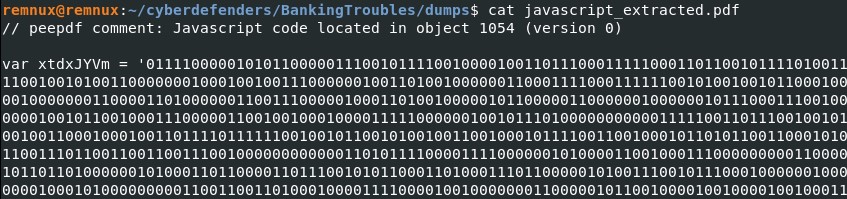
The JavaScript will be extracted in the file "javascript_extracted.pdf". Let's run peepdf.
peepdf -f -s extractjs.txt file.None.0x82091008.dat
Process winlogon.exe hosted a popular malware that was first submitted for analysis at VirusTotal on 2010-03-29 11:34:01. Provide the MD5 hash of that malware.
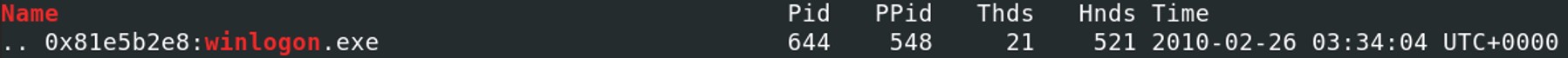
Let's check if the system has run the process winlogon.exe at the time when the memory image has been taken.Vol.py -f Bob.vmem –profile=WinXPSP2x86 pstree | egrep “^Name|winlogon”
 A winlogon process is running in the system, malfind is a volatility plugin that searches for malicious executables, dlls or shellcode inside of the process.
A winlogon process is running in the system, malfind is a volatility plugin that searches for malicious executables, dlls or shellcode inside of the process.
Vol.py -f Bob.vmem –profile=WinXPSP2x86 malfind -p 644 -D ./winlogon
Malfind has extracted 6 subprocesses from winlogon. Running file to determine the type of file.
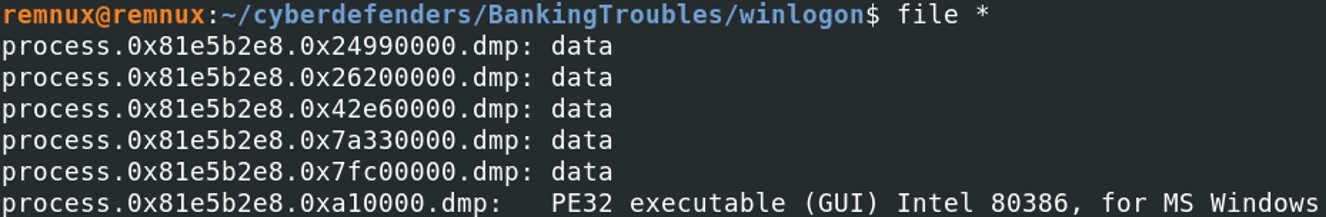 One process is seen as a PE file, let's calculate the hash of that file. I've renamed the file as winlogon.exe to simplify the command.
One process is seen as a PE file, let's calculate the hash of that file. I've renamed the file as winlogon.exe to simplify the command.
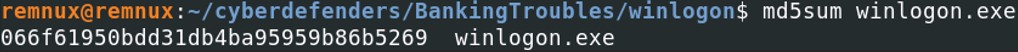 MD5 hash : 066f61950bdd31db4ba95959b86b5269
MD5 hash : 066f61950bdd31db4ba95959b86b5269
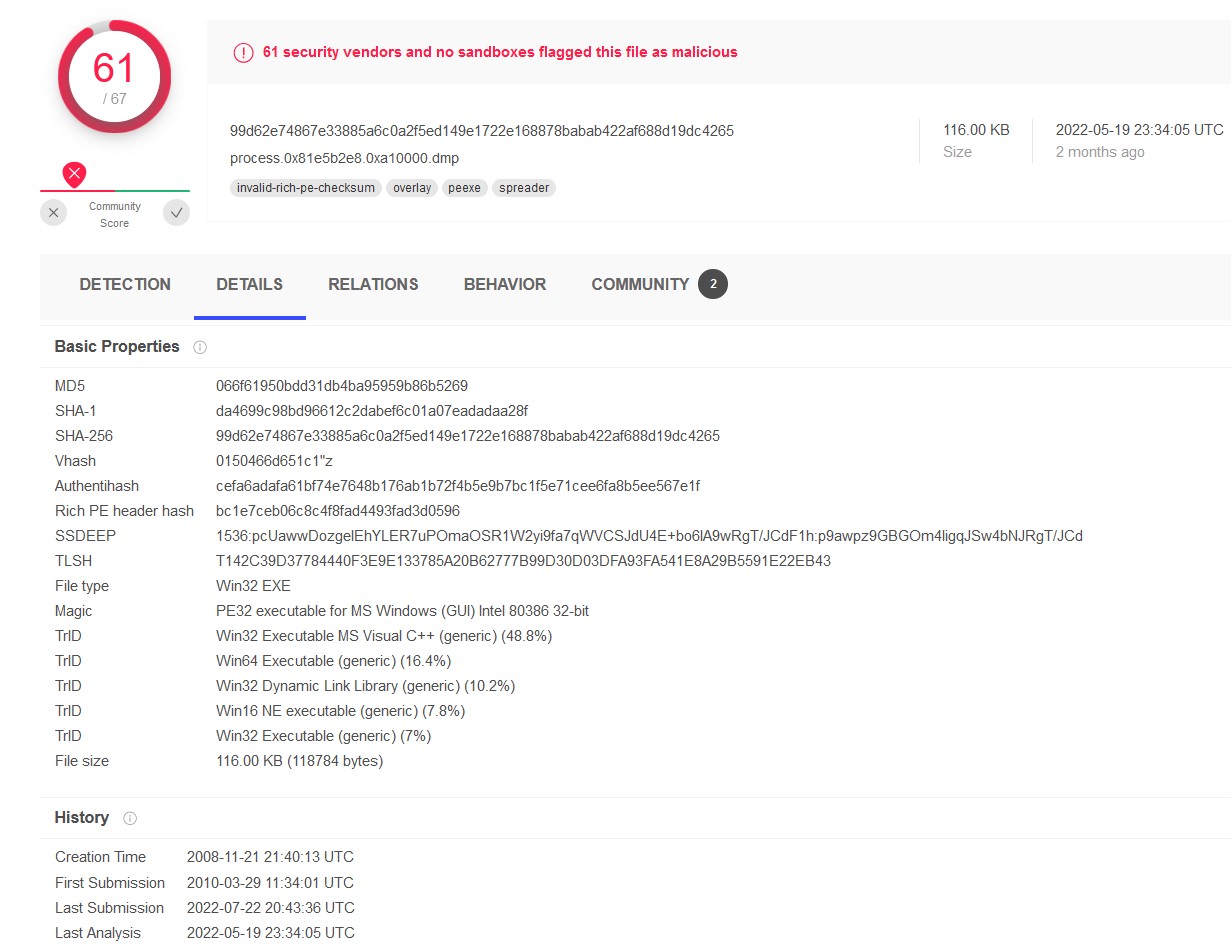
What is the name of the malicious executable referenced in registry hive '\WINDOWS\system32\config\software', and is variant of ZeuS trojan?
Hivelist plugin displays the registry hives from the memory images. The windows registry hives are located in the folder C:\Windows\System32\config.vol.py -f Bob.vmem --profile=WinXPSP2x86 hivelist | grep software
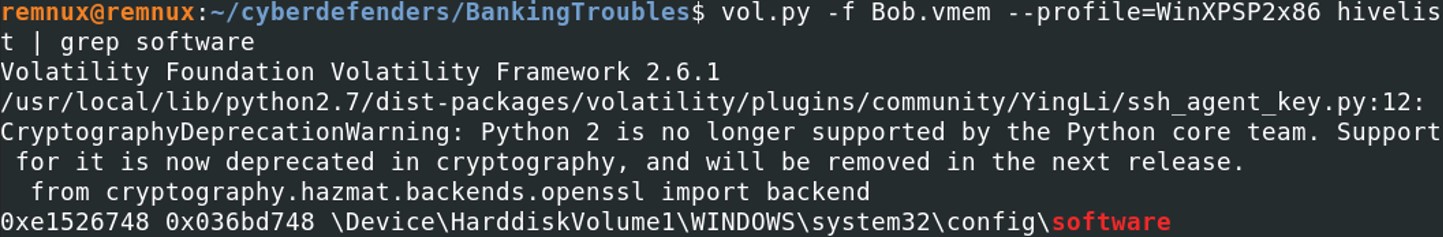 The virtual address of the registry is 0xe1526748. The printkey plugin will display the subkeys of the hive.
The virtual address of the registry is 0xe1526748. The printkey plugin will display the subkeys of the hive.
vol.py -f Bob.vmem --profile=WinXPSP2x86 -o 0xe1526748 printkey
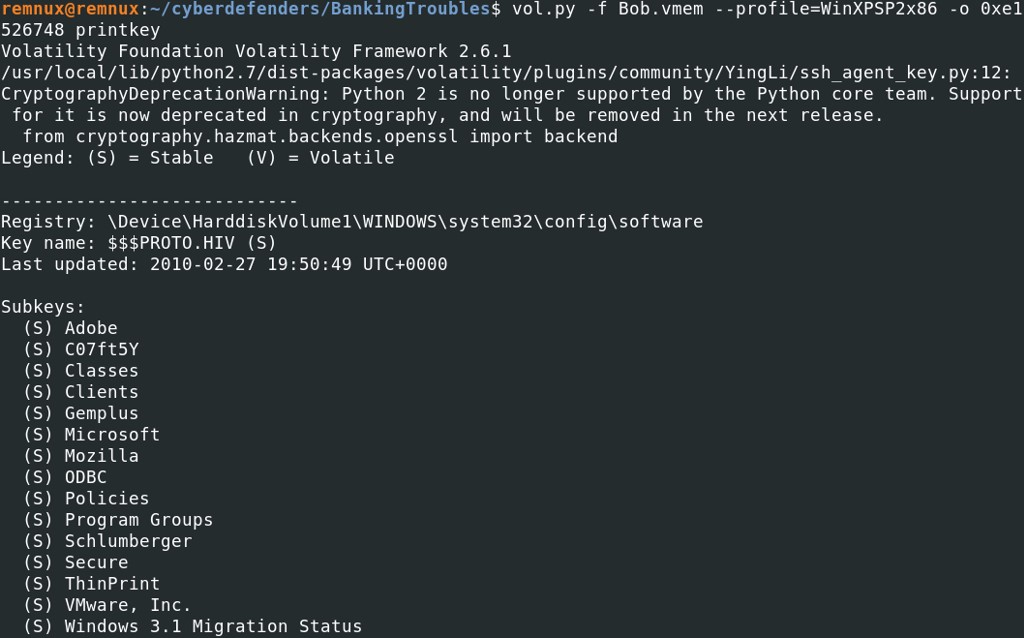 One of the persistence techniques with Winlogon.exe is located at the registry subkey “Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit”. The values of this key are usually .exe files, because it defines which programs are run by Winlogon when a user logs in to the system.
One of the persistence techniques with Winlogon.exe is located at the registry subkey “Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit”. The values of this key are usually .exe files, because it defines which programs are run by Winlogon when a user logs in to the system.
vol.py -f Bob.vmem --profile=WinXPSP2x86 printkey -o 0xe1526748 -K "Microsoft\Windows NT\CurrentVersion\Winlogon"
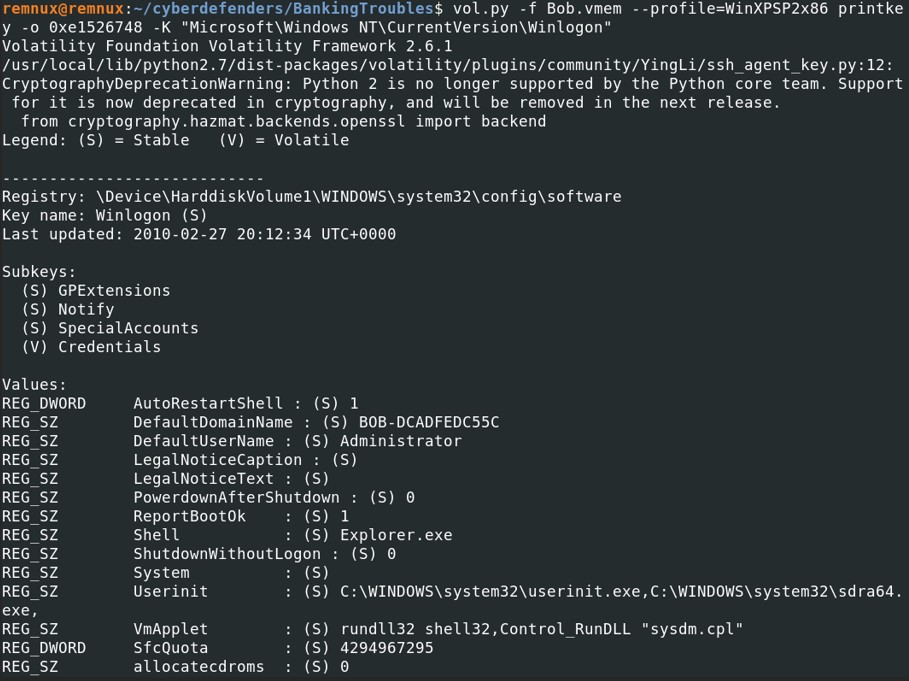 Among the executable files in the key “Userinit”, we have userinit.exe and sdra64.exe. Let's extract sdra64.exe to find out if this is malicious or not.
Among the executable files in the key “Userinit”, we have userinit.exe and sdra64.exe. Let's extract sdra64.exe to find out if this is malicious or not. vol.py -f Bob.vmem --profile=WinXPSP2x86 filescan | grep sdra64.exe
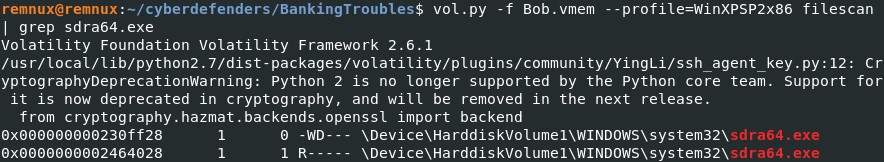 Virtual address location of the file : 0x0000000002464028, let's dump it with dumpfiles.
Virtual address location of the file : 0x0000000002464028, let's dump it with dumpfiles.
vol.py -f Bob.vmem --profile=WinXPSP2x86 dumpfiles -Q 0x0000000002464028 -D ./dumps
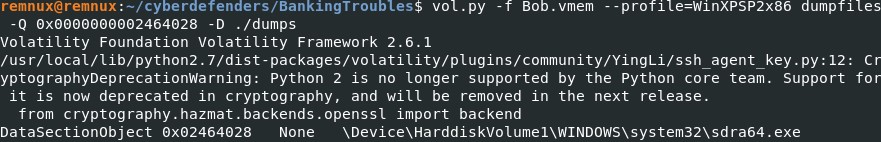
md5sum sdra64.exe
b3e40cb29a3125ac862570ed5b5212a5 sdra64.exe
b3e40cb29a3125ac862570ed5b5212a5 sdra64.exe