How does it work ?
Whenever Symantec Endpoint Protection quarantines a file, a .vbn file is created on the local machine under the path “C:\ProgramData\Symantec\Symantec Endpoint Protecton\[VERSION_NUMBER]\Data\Quarantine”.
Thanks to the tool "vbntool.py", a python script that can parse the information of the .vbn file and help us recover the quarantine file or get more information about the quarantine file.
Here's the link of the project : https://github.com/SkallZou/vbntool
POC : Quarantine file recovery
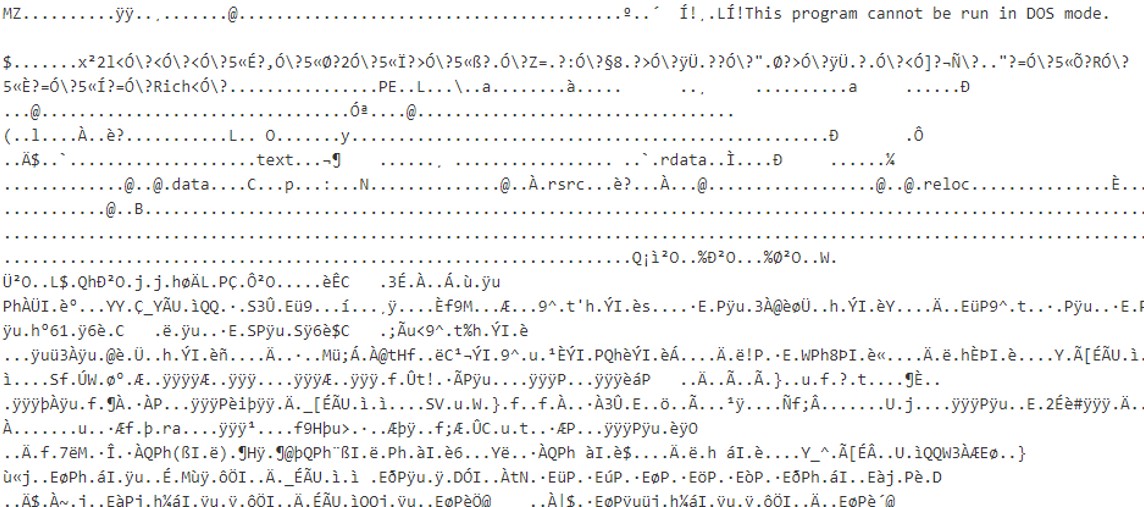 The content above represents mimikatz.exe and will probably be flagged as malicious by Symantec Endpoint Protection.
The content above represents mimikatz.exe and will probably be flagged as malicious by Symantec Endpoint Protection.
Download this content as download.dat.
SEP detected it and quarantined it. In the same tme I've made another test with mimikatz.exe, SEP detected it as well and quarantined it likewise.
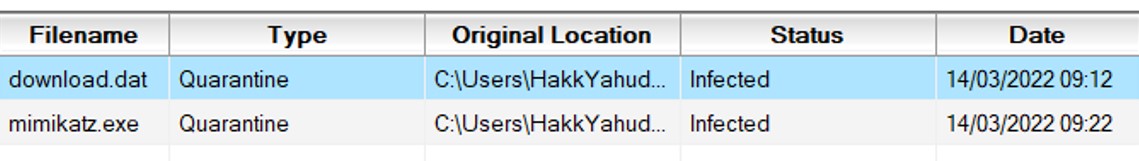 Two qurantine files mean two .vbn files under the path C:\ProgramData\Symantec\Symantec Endpoint Protecton\[VERSION_NUMBER]\Data\Quarantine right ?
Two qurantine files mean two .vbn files under the path C:\ProgramData\Symantec\Symantec Endpoint Protecton\[VERSION_NUMBER]\Data\Quarantine right ?
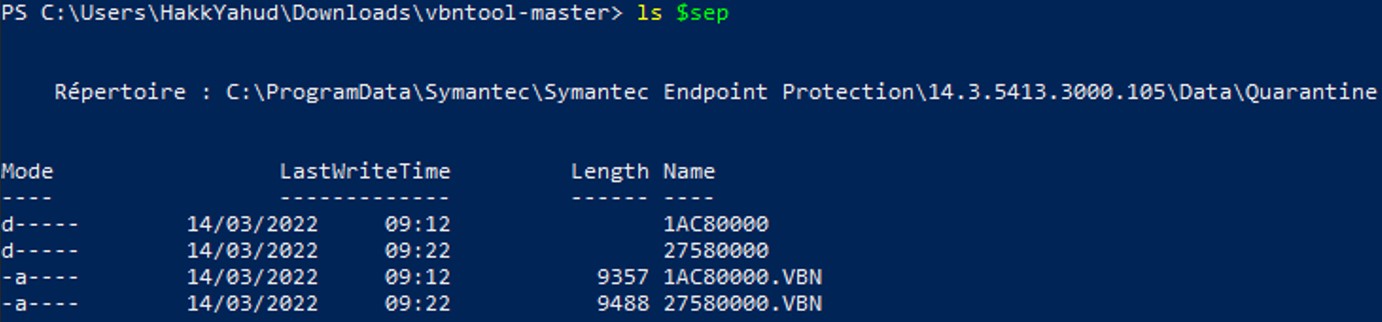 We've got the 2 .vbn file under the folder, the run vbntool to see what kind of information does it provide.
We've got the 2 .vbn file under the folder, the run vbntool to see what kind of information does it provide.
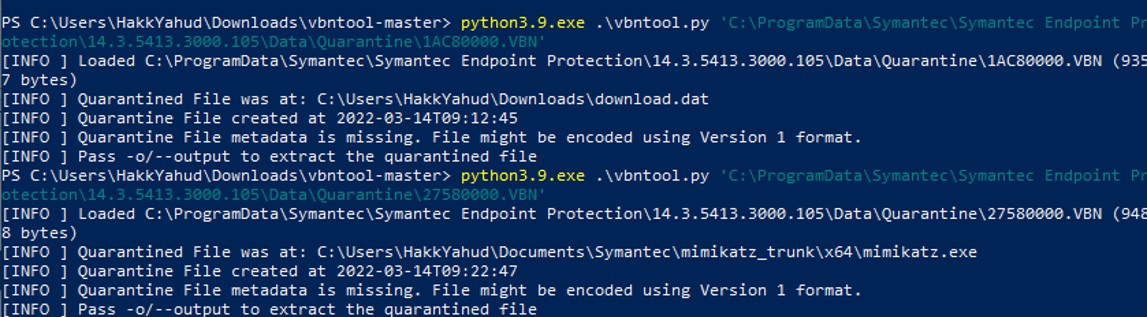 The time stamp is matching perfectly the quarantine time of both files.
The time stamp is matching perfectly the quarantine time of both files.
Let's extract the both quarantine file. Pass -o/--output to extract the quarantine file
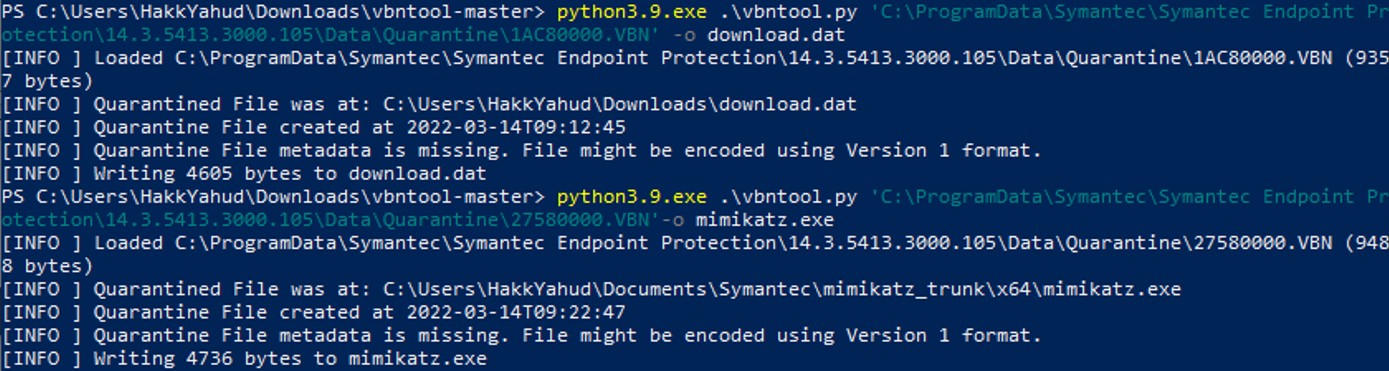 Surprisingly, SEP didn’t raise an alert to quarantine te file again. Moreover only 4ko for a mimikatz is really small, which is strange.
Surprisingly, SEP didn’t raise an alert to quarantine te file again. Moreover only 4ko for a mimikatz is really small, which is strange. Let's check the hex dump.
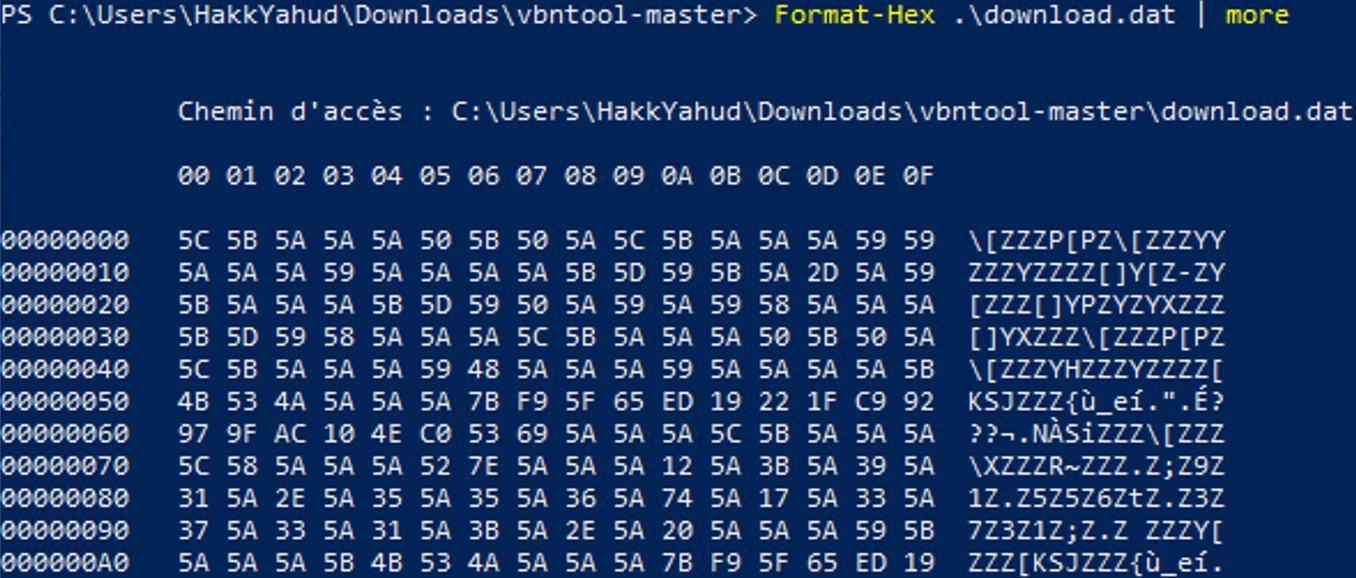
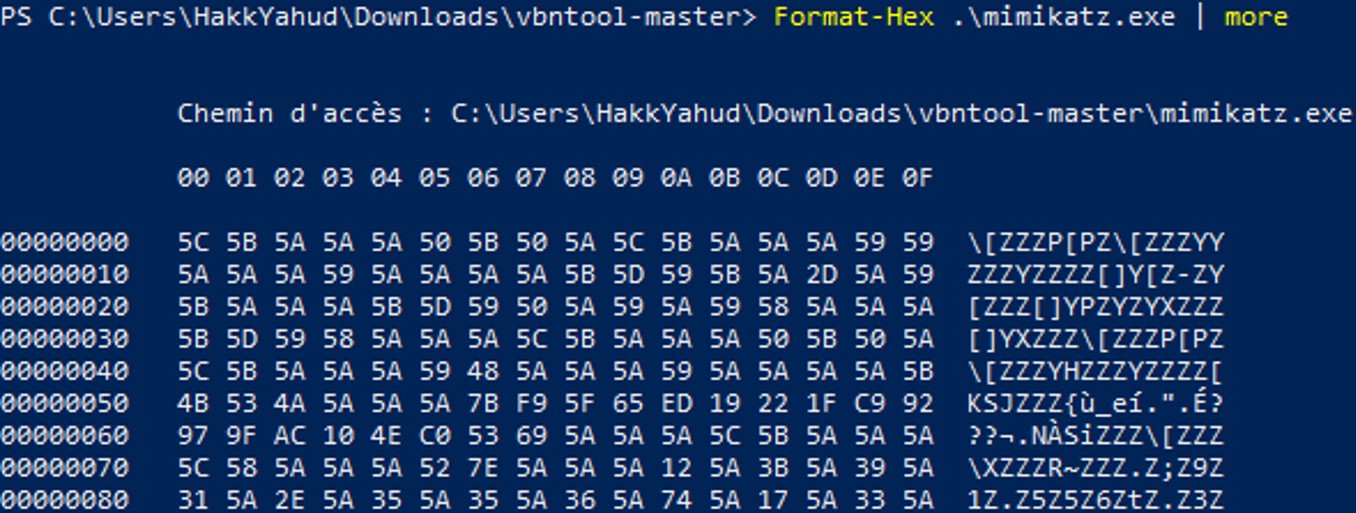 A exe file should always start with the magic byte MZ (4D5A). Therefore I suspect that there are some encryption made by Symantec or some errors, this is why SEP didn’t quarantine the file again.
A exe file should always start with the magic byte MZ (4D5A). Therefore I suspect that there are some encryption made by Symantec or some errors, this is why SEP didn’t quarantine the file again. Taking another look at the Quarantine folder, we don't only have those .vbn files but some folders are presents with their respective names.
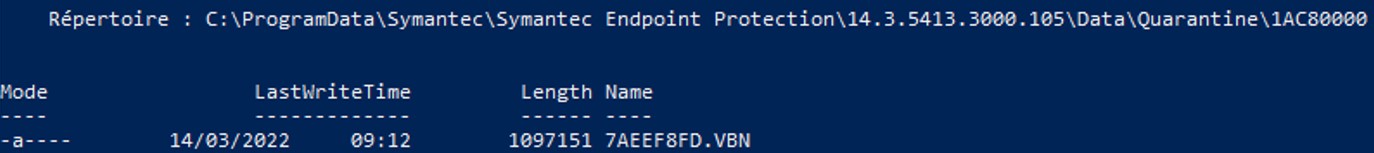 Another .vbn file is found inside of that folder. Let's run vbntool to see what information do we get.
Another .vbn file is found inside of that folder. Let's run vbntool to see what information do we get.
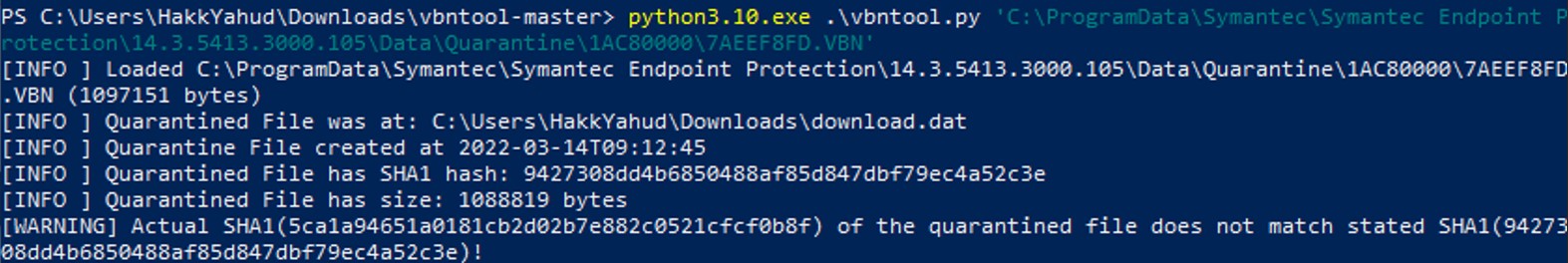 It gives the same metadata, except that the actual hash of the quarantined file does not match with the hash of that .vbn file. Let's extract it.
It gives the same metadata, except that the actual hash of the quarantined file does not match with the hash of that .vbn file. Let's extract it.
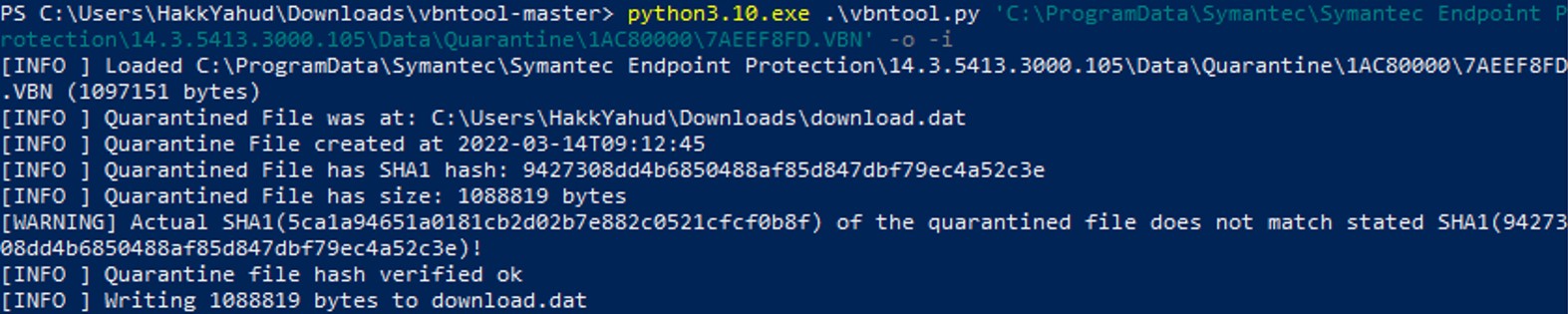 In the second attempt, more bytes are written in the download.dat file.
In the second attempt, more bytes are written in the download.dat file. Let's take another look to the hexdump.
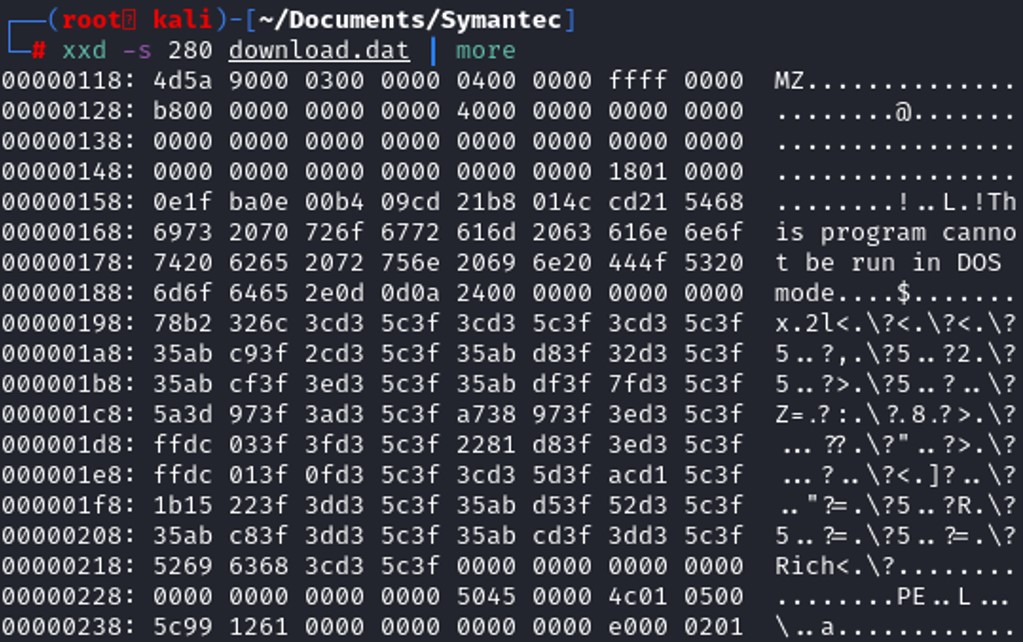
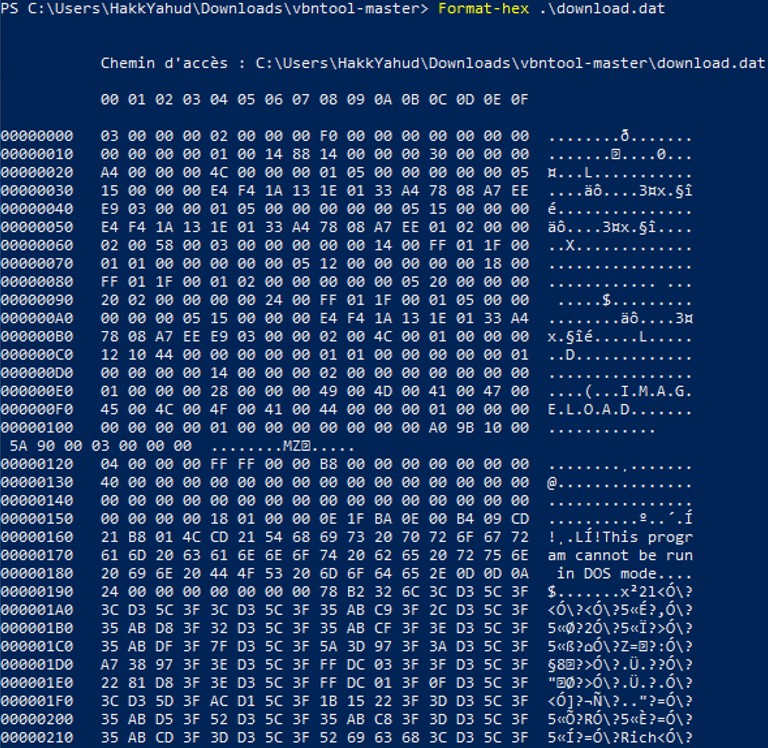 Looking at the hex dump, we see the MZ byte is present, despite the fact we don’t see 4D5A but only 5A. Sending the file to a Linux system to have a better tool to cut hexdump.
Looking at the hex dump, we see the MZ byte is present, despite the fact we don’t see 4D5A but only 5A. Sending the file to a Linux system to have a better tool to cut hexdump.
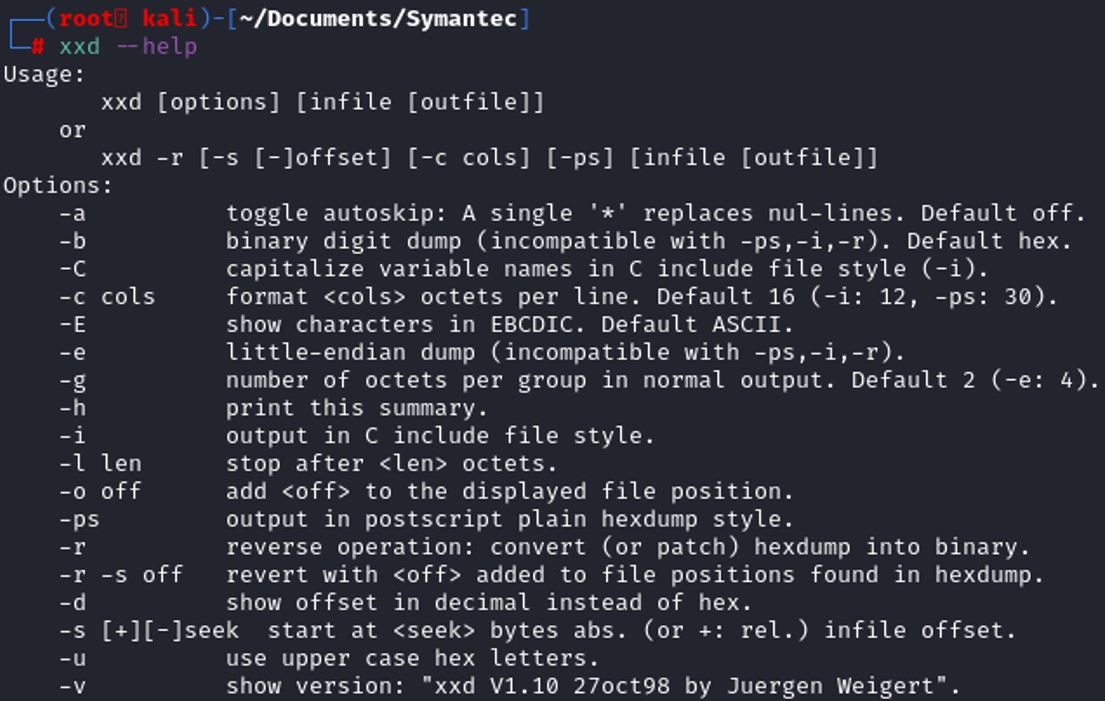
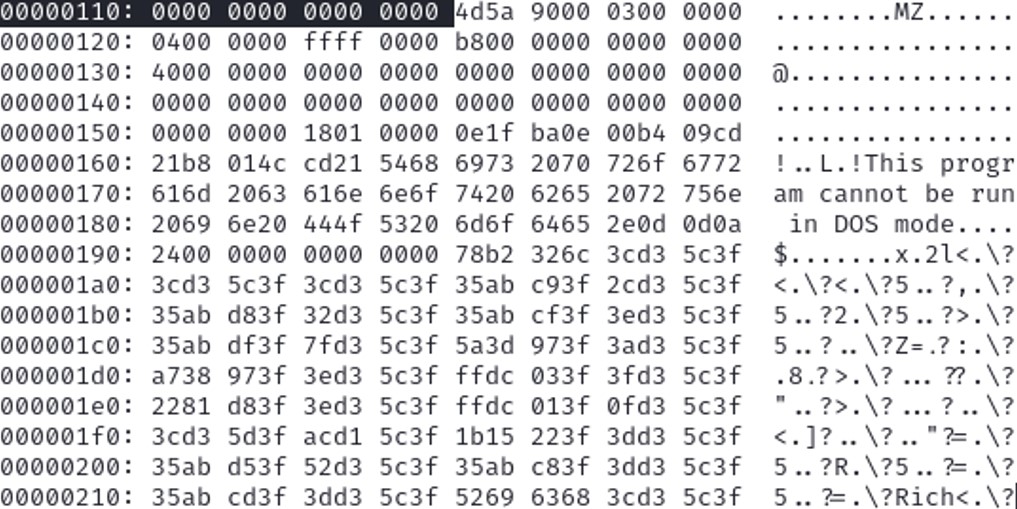 The offset that we need to take into account, to cut until the MZ byte is 118. We need to convert 118 to decimal.
The offset that we need to take into account, to cut until the MZ byte is 118. We need to convert 118 to decimal.
280
 Time to redirect to another file. Redirect only the hex on a file call mimikatz.
Time to redirect to another file. Redirect only the hex on a file call mimikatz.
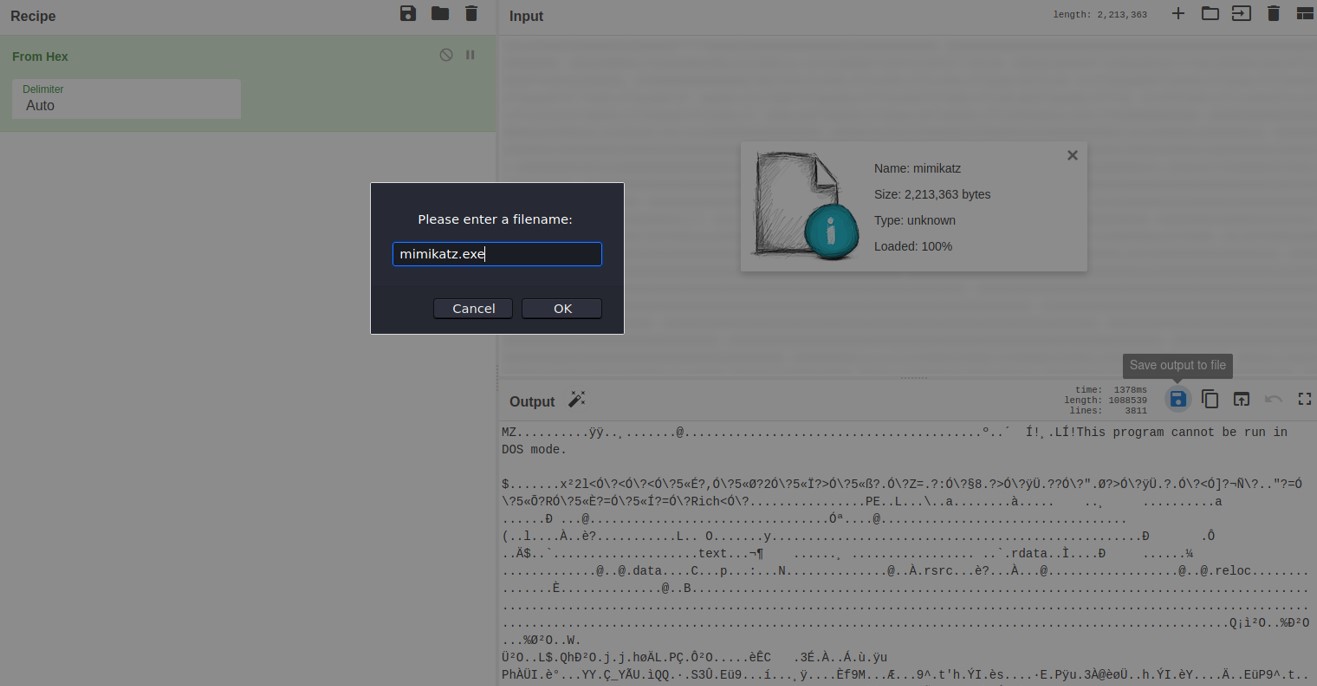 Get the file hash of the recovered mimikatz.exe.
Get the file hash of the recovered mimikatz.exe.
363a14d0604b63ffc04abadca139ed16 mimikatz.exe
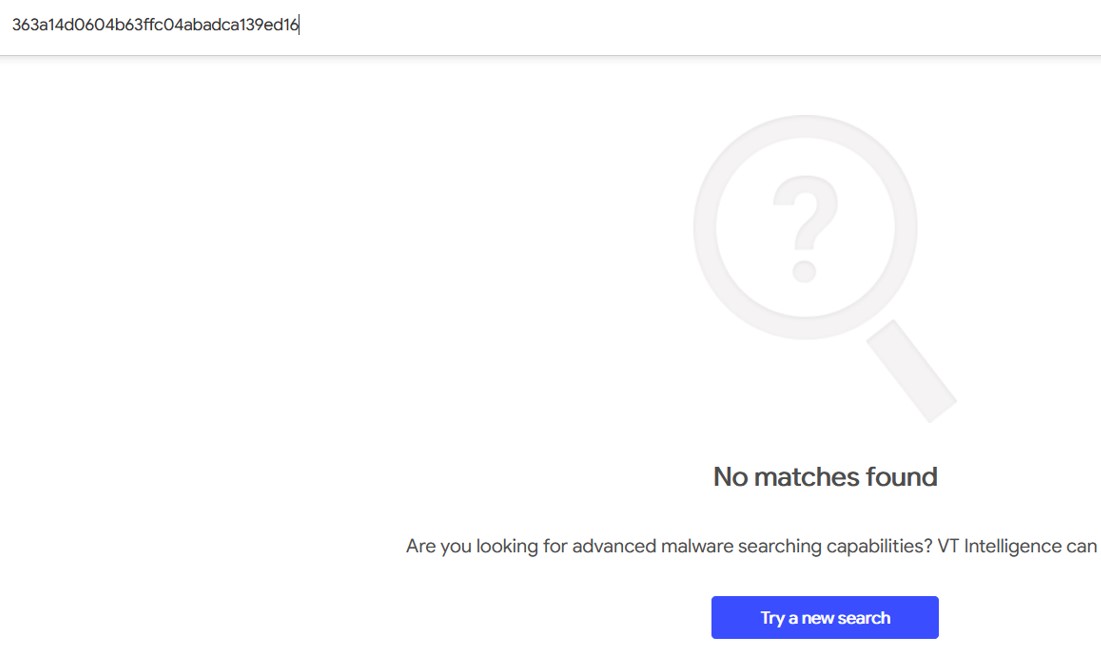 Hash not found in VirusTotal, seems like we couldn’t get the file back… Sending the file to the Windows machine to confirm.
Hash not found in VirusTotal, seems like we couldn’t get the file back… Sending the file to the Windows machine to confirm.
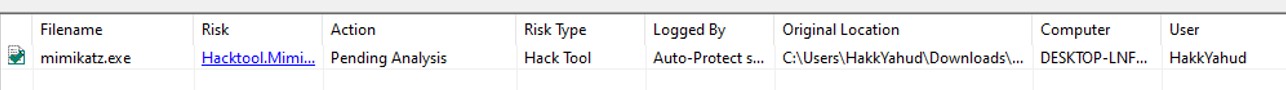 Ohhhh... Wait a moment, SEP detected it as mimikatz ! We might have recovered the quarantine file from the .vbn file. Let's put an exclusion on the destination folder, and run mimikatz.exe
Ohhhh... Wait a moment, SEP detected it as mimikatz ! We might have recovered the quarantine file from the .vbn file. Let's put an exclusion on the destination folder, and run mimikatz.exe
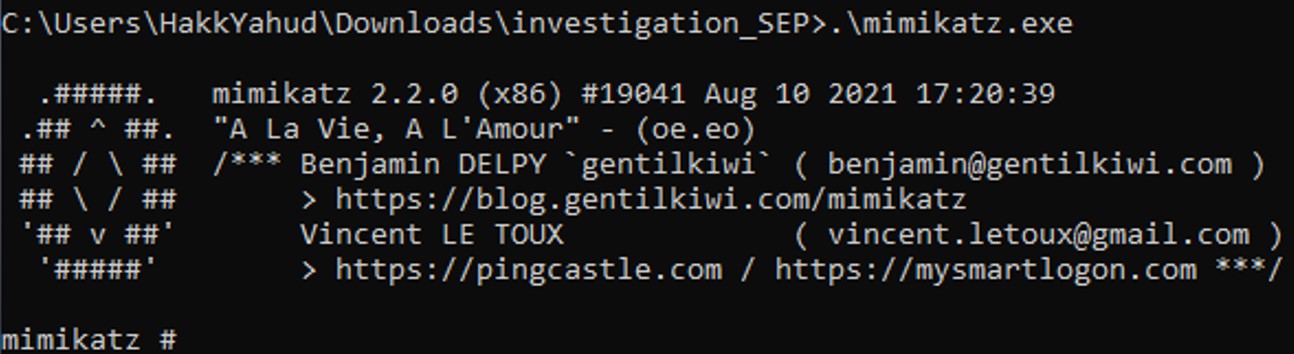 Mimikatz is running, we managed to recover the quarantine file from those .vbn file under the path C:\ProgramData\Symantec\Symantec Endpoint Protecton\[VERSION_NUMBER]\Data\Quarantine.
Mimikatz is running, we managed to recover the quarantine file from those .vbn file under the path C:\ProgramData\Symantec\Symantec Endpoint Protecton\[VERSION_NUMBER]\Data\Quarantine.
UPDATE : Deleted file can also be recovered from SEP
A new test has been done with a malicious .pdf
The .pdf file has been detected and cleaned (deleted) by Symantec Endpoint Protection.
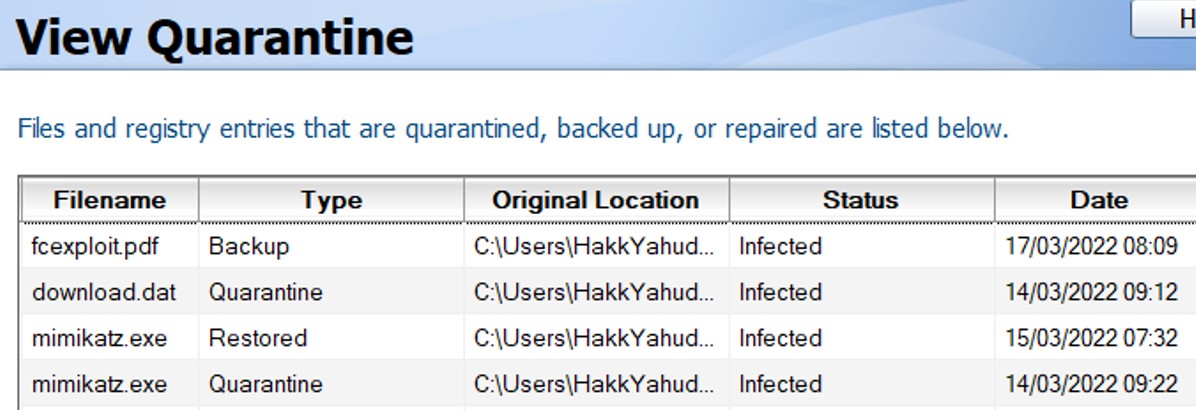 As usual we have the .vbn file and a folder that has the same name. From the previous experience, we know if the .vbn has a folder with a similar name, we will not take that .vbn file into account but get the .vbn file inside of that folder.
As usual we have the .vbn file and a folder that has the same name. From the previous experience, we know if the .vbn has a folder with a similar name, we will not take that .vbn file into account but get the .vbn file inside of that folder.
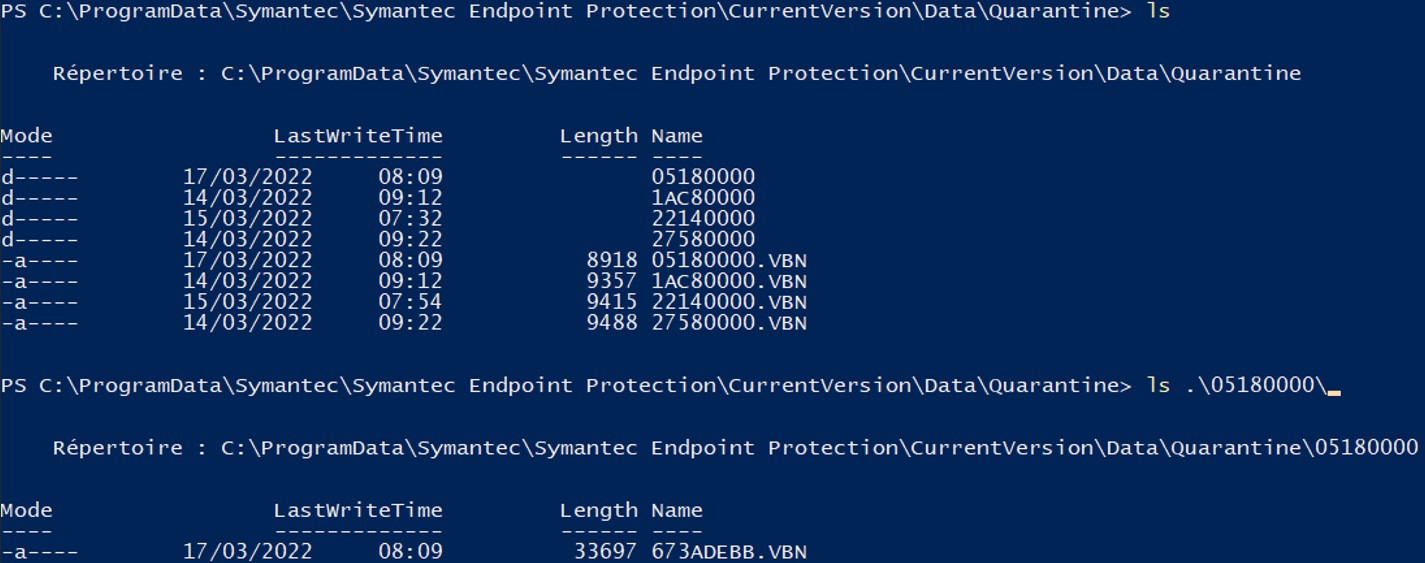 The option "-l" of "vbntool" gives more details and more information about the file that has been deleted or put in quarantine.
The option "-l" of "vbntool" gives more details and more information about the file that has been deleted or put in quarantine.
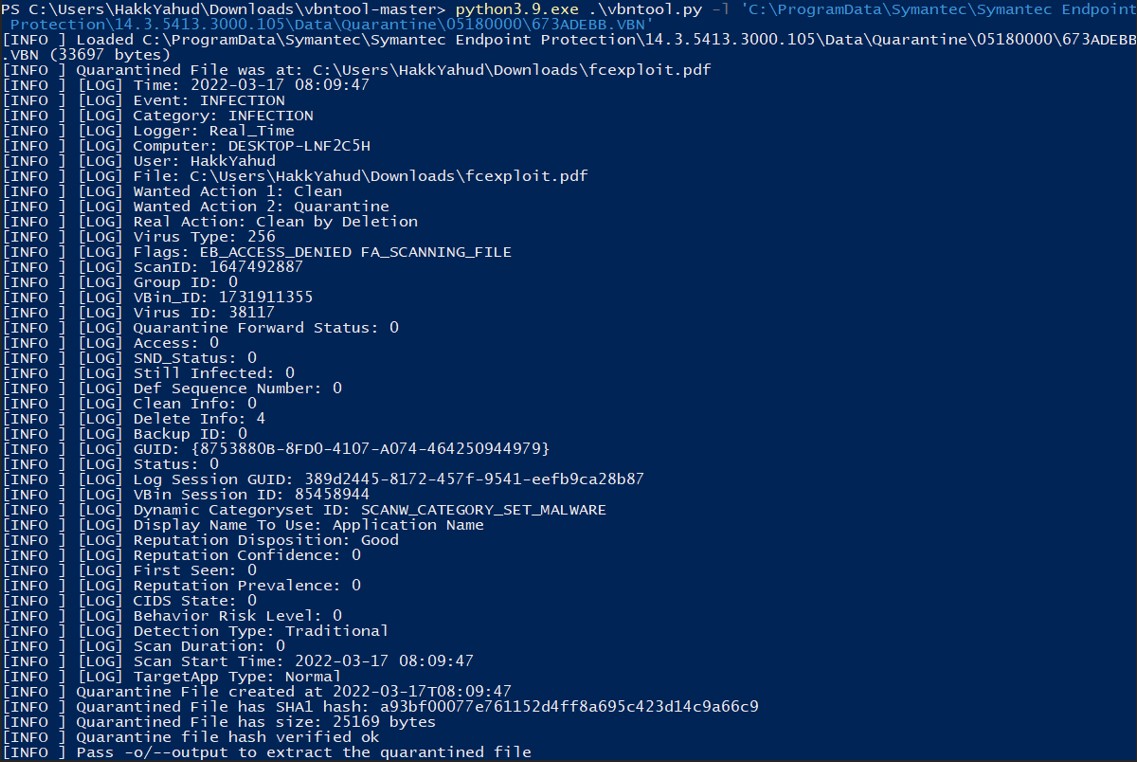 Let's extract the quarantine file and name it as fcexploit_extracted.pdf
Let's extract the quarantine file and name it as fcexploit_extracted.pdf
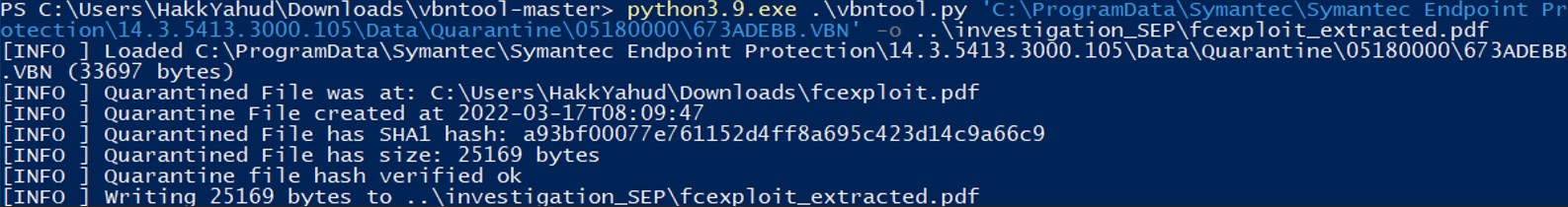 Notice that this time that we don’t get the warning about the actual file hash is different from the quarantine file hash.
Notice that this time that we don’t get the warning about the actual file hash is different from the quarantine file hash.
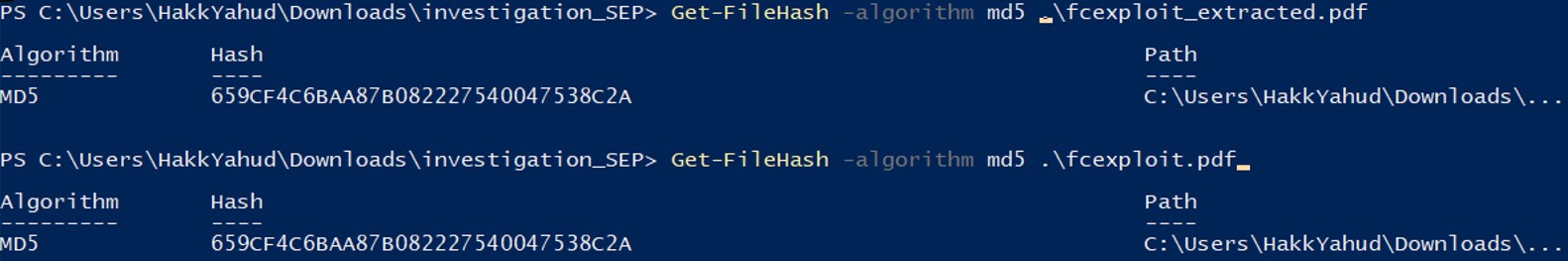 The recovered file has the same hash file as the original one. It seems that with a pdf file, we don’t need to do any hexadecimal cutting.
We have recovered those file that has been cleaned by Symantec Endpoint Protection.
The recovered file has the same hash file as the original one. It seems that with a pdf file, we don’t need to do any hexadecimal cutting.
We have recovered those file that has been cleaned by Symantec Endpoint Protection.
Conclusion : Lesson learnt
Many .vbn files can be found under the path “C:\ProgramData\Symantec\Symantec Endpoint Protection\[VERSIONNUMBER]\Data\Quarantine\”. Make sure that the .vbn file that you pick does not have a folder with the same name, otherwise the hexdump will show you some incorrect hex.
Before extracting the file, make sure to check the information of the quarantine file to know what kind of file is.
.exe, .pdf, .xlsx have different signatures, it will be useful to know those signature when editing the hexdump.
List of file signatures - Wikipedia